phishing of social networks via Setoolkit
Kali linux has such a cool thing as the Social Engineering Toolkit , and we will do it
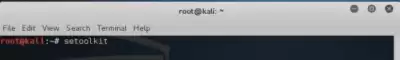
1. Open the terminal in Kali and write the setoolkit command, it will look like this.
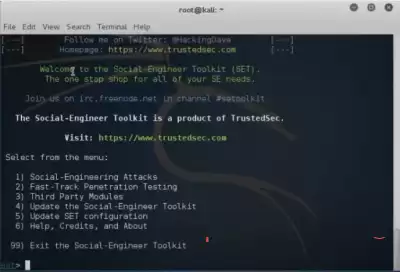
2. after our "Program" is loaded, we get about this.
3. From here we need to go to Social-Engineering Attacks, so we prescribe "1"
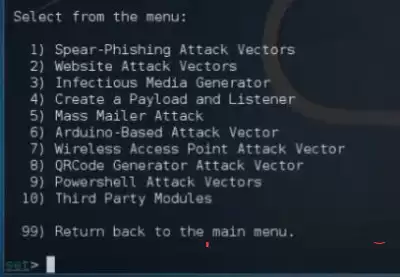
This Menu will open.
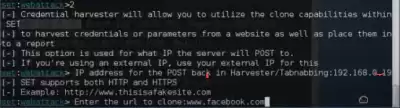
4. Here we need to go to the Website Attack Vectors , therefore we write in the line "2"
There will be such a menu.
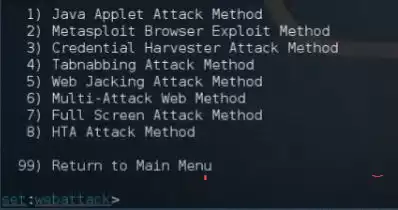
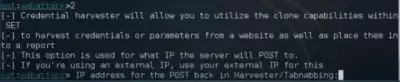
5. We need the Credential Harvester Attack method, we prescribe "3"
This menu opens
6. Here it's clear to the hedgehog, we need a Site Cloner, So we prescribe "2"
here we register our IP Address and press Enter
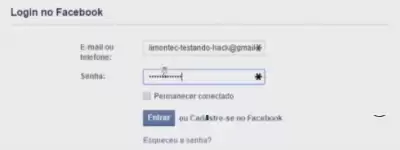
7. In the line that opens, we write the Full Address of the page that we want to copy
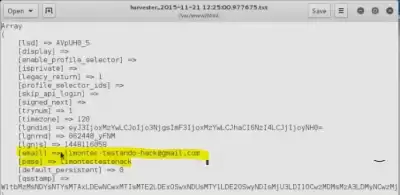
Now We Are Testing
****aem there any text in the login and password windows

 Spain
Spain
 Portugal
Portugal