How to protect your cloud server (Ubuntu and CentOS)?

You can spend time on firewall security, cloud security, etc., but leaving the OS unprotected can be dangerous.
The network is moving to the cloud from shared hosting, which provides many advantages.
Faster response time because resources are not being used by other users
Full control over the technology stack
Full control over the operating system
Budget
You get more control over hosting your site on a cloud virtual machine, but some system administrator skills are required to manage your virtual machine.
Let's move on to the practical Ubuntu and CentOS VM security guide.
1. Changing the standard SSH port
By default, SSH listens on port 22. This means that if someone discovers your IP address, they will be able to connect to your server
They may not be able to access your server if you are protected by a complex password. However, they can launch brute force attacks to disrupt the server.
It's best to change the SSH port to something else, so even if someone knows the IP address, they won't be able to try to connect using the default SSH port.
Changing the SSH port on Ubuntu/CentOS is very simple.
Log in to your virtual machine with superuser rights (sudo)
Make a backup of sshd_config (/etc/ssh/sshd_config)
Open the file using the VI editor (the editor is at your discretion)
vi/etc/ssh/sshd_config
Look for a line that has the value Port 22 (usually at the beginning of the file)
# What ports, IPs and protocols we listen for
Port22
Replace 22 with another number (remember, as you will need it to connect). Let's say 5,000
Port5000
Save the file and restart SSH.
servicesshd restart
Now you or anyone else will not be able to connect to your server via the default SSH port (22). Instead, you can use the new port to connect.
If you are using an SSH client or Terminal on a MAC, you can use -p to determine the user port.
ssh-p 5000 username@128.199.100.xxx
2. Protection against brute-force attacks
One of the common mechanisms used by a hacker to gain control of your server is to initiate brute force attacks on the server and a web platform such as WordPress, Joomla, etc.
This can be dangerous if not taken seriously. There are two popular programs that you can use to protect Linux from Brute-force.
SSH Guard
SSHGuard monitors running services from system log files and blocks repeated failed login attempts.
It was originally intended to protect SSH login, but now it supports many others.
Pure FTP, PRO FTP, VS FTP, FreeBSD FTP
Exim
Sendmail
Dovecot
Cucipop
UWimap
You can install SSHGuard using the following commands.
Ubuntu:
apt-get install SSHGuard
CentOS:
wget ftp://ftp.pbone.net/mirror/ftp5.gwdg.de/pub/opensuse/repositories/home:/hornos:/centos/CentOS_CentOS-6/x86_64/sshguard-1.5-7.1.x86_64.rpm rpm -ivh sshguard-1.5-7.1.x86_64.rpm
fail2ban
Fail2Ban is another popular SSH protection program. Fail2Ban automatically updates the iptables rules if a failed login attempt reaches a certain threshold.
Installing fail2ban:
Ubuntu:
apt-get install fail2ban
CentOS:
yum install epel-release
yum install fail2ban
SSHGuard and Fail2Ban should be enough to protect SSH login. However, if you need to learn more, you can refer to the following services.
CSF (ConfigServer Security & Firewall)
DenyHosts
3. Disable password-based authentication
If you log in to the server from one or two computers, you can use SSH key authentication.
However, if you have multiple users and you often log in from multiple public computers, key exchange can be problematic every time.
Therefore, depending on the situation, if you decide to disable password-based authentication, you can do so as follows.
Note: It is assumed that you have already configured SSH key exchange.
Edit the /etc/ssh/sshd_config file using the vi editor (the editor is at your discretion)
Add the following line or uncomment it if it exists
PasswordAuthenticationno
Restart SSHD
4. Protection against DDoS attacks
DDoS (Distributed Denial of Service) can happen at any level, and that's the last thing you want to have as a business owner.
Searching for the source IP address is possible, and as a best practice, you should not disclose the IP address of your server to the public Internet. There are several ways to hide the Source IP to prevent DDoS on your server.
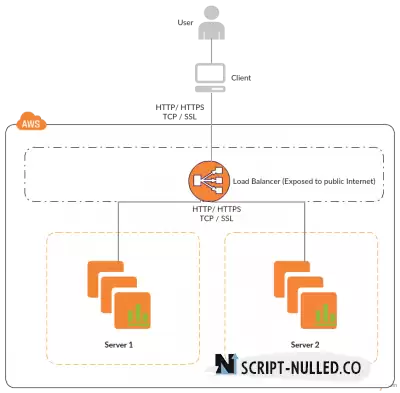
Use a load balancer (LB)
Implement a load balancer with Internet access so that the IP address of the server is not open to the network. There are many load balancers available: Google Cloud LB, AWS ELB, Linode Node balance, DOB, etc.
Use
CDN (Content Delivery Network) - one of the best ways to improve the performance and security of a website.
When implementing a CDN, you configure a DNS record with an arbitrary IP address provided by the CDN provider. By doing this, you advertise the IP address of the CDN provider for your domain, but the source is not disclosed.
There are many CDN providers to speed up the site, protect against DDoS, WAF and many other functions.
Cloudflare
Amazon CloudFront
SUCURI
KeyCDN
So choose a CDN provider that provides performance and security.
Configure the iptables settings
You can use iptables to block suspicious requests, SYN, fake TCP flag, private subnet, and more.
Use a firewall
If you provide a hardware firewall, then fine, otherwise you can use a software firewall that uses iptables to protect the incoming network connection to the VM.
There are many of them, but one of the most popular is UFW (Uncomplicated Firewall) for Ubuntu and FirewallD for CentOS.
5. Regular backups
Backup is your friend! When nothing is working, a backup will save you.
Things may not go this way, but what if you don't have the necessary backup to restore? Most cloud or VPS providers offer backups for a small additional fee, and this should always be remembered.
Ask your VPS provider how to enable the backup service. If you use Google Compute Engine or AWS, schedule a daily snapshot.
A backup will allow you to quickly restore the entire virtual machine, and you will be back in business again.
6. Regular updates
Constantly updating the operating system of a virtual machine is one of the most important tasks so that your server is not exposed to any recent security vulnerabilities.
In Ubuntu, you can run apt-get update to make sure that the latest packages are installed.
In CentOS, you can use yum update
7. Do not leave ports open
In other words, allow only the necessary ports.
Keeping unwanted ports open is desirable for an attacker. If you are just hosting your site on your virtual machine, then most likely you need port 80 (HTTP) or 443 (HTTPS).
If you are using AWS, you can create a security group to allow only the necessary ports and associate them with the VM.
If you are using Google Cloud, allow the necessary ports using "Firewall rules".
Conclusion
The above should help you strengthen and secure your server to better protect against online threats.

 Spain
Spain
 Portugal
Portugal