Bypassing Windows Defender cheap and angry: meterpreter session via python
Hello everyone. Today we will consider the option of running a meterpreter session on a Windows 10 machine with the latest patches (including Windows Defender). And we will also bypass antiviruses.
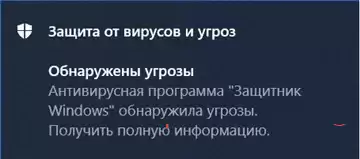
We are getting a warning from our old friend Windows Defender, whom we all love so much.
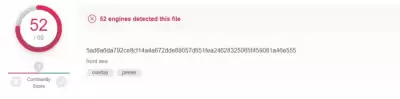
If we ask VirusTotal, he will say the following:
Let's run Python and do what we're all here for.
Python/meterpreter/reverse_tcp is a unique cross-platform payload Metasploit Framework that allows you to remotely control a compromised computer. There is no need to think about which platform to choose, it will work on any, but in this case we will make an executable file for Windows from it.
To begin with, install the py2exe package, which allows you to make a Windows executable file from a Python script.
We will have Python 3.4 (everything above does not support py2exe).
py -3.4 –m pip install py2exe
or
pip install py2exe
Next, we will create a "raw" python code with the .py extension
Let's go ahead and make sure that the session is working correctly.
As a result, I note that the python meterpreter shell is inferior in functionality to the more familiar windows meterpreter. For example, you won't be able to migrate to a process or use commands like getsystem, but it's still a real alternative.: get a session to work with msf (routing and portfwd at least) and continue to work inside the network.

 Spain
Spain
 Portugal
Portugal