Creating malicious QR codes to hack phones and other devices
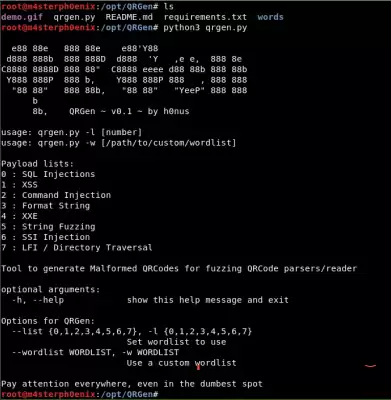
Installing QRGen
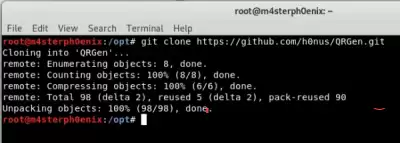
First we need to download the repository from github.
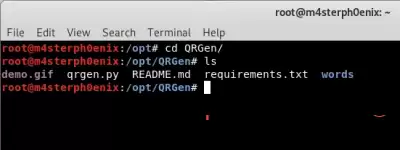
After downloading, change the directory using cd.
cd /QRGen
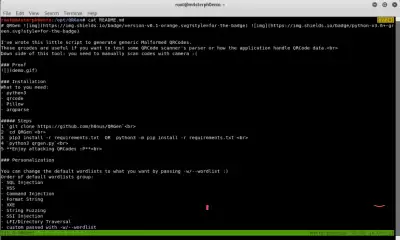
Let's look at the file README.md .
Now we need to install some requirements and libraries that are required for QRGen.
pip3 install -r requirements.txt
If this command doesn't work, there is another alternative.python3 -m pip install -r requirements.txt
Creating a malicious QRcode from a payload
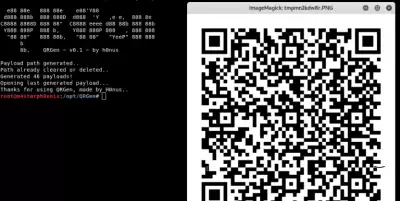
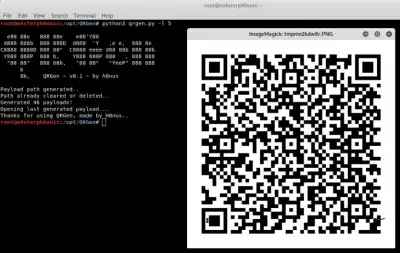
Now that we have installed QRGen, we will run it to generate our example malicious load.
python3 qrgen.py
As you can see, it is easy to generate a payload.
python3 qrgen.py -l 5
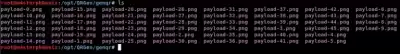
A series of QR codes will be generated, and the last one created will open automatically.
cd genqr
Let's scan our QR code and see.
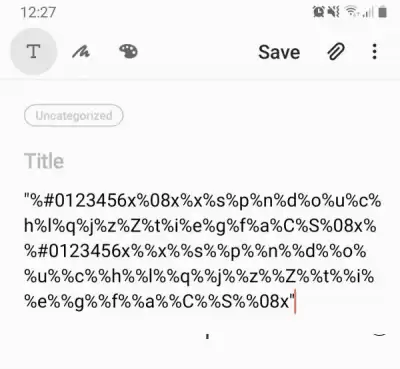 Note: Information for research, training, or auditing. Use for mercenary purposes is punishable by law.
Note: Information for research, training, or auditing. Use for mercenary purposes is punishable by law.

 Spain
Spain
 Portugal
Portugal