Hacking routers and finding their location
Keep in mind, illegal entry is punishable by law.The channel is not responsible
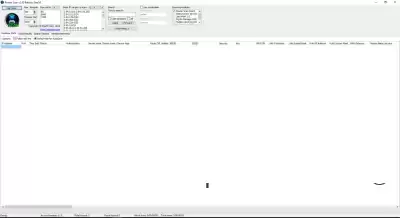
First we need the RouterScan program:
The program can be installed by unpacking files from the archive to a specified folder. The program performs an attack on ports
80
8080
1080
We consider this to be quite justified in the list requiring no additional changes.
In addition, the program has the ability to connect additional modules. But such a busy program will significantly slow down its work. Therefore, we will not touch anything in this window. After all, the purpose of the attack is to access the web interface of one random router.
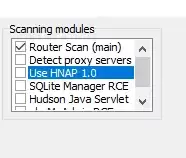
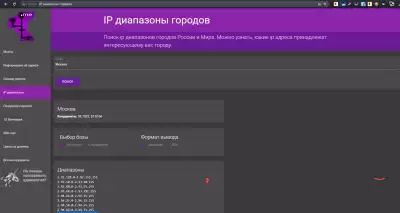
Copy the required number of ranges, and go to the program
3. Insert ranges here:
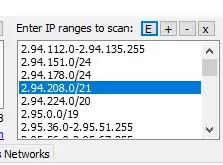
4. Click on start:
5.All successful attempts will be displayed in the Good results tab
Here we will see the login details
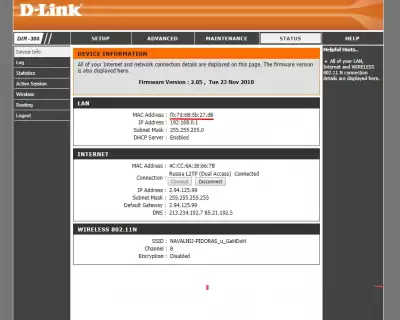
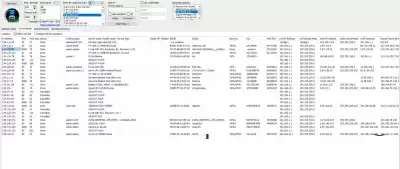 6.In the Status tab, We find the mac address of the access point:
6.In the Status tab, We find the mac address of the access point:
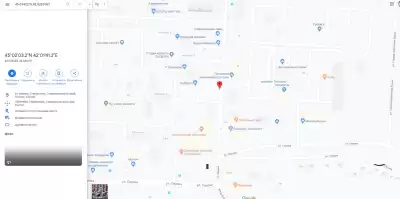
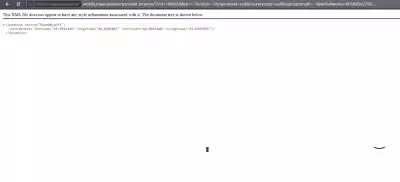 8.Go to Google / Yandex maps, enter the coordinates.First Latitude/Latitude, then longitude/longitude
8.Go to Google / Yandex maps, enter the coordinates.First Latitude/Latitude, then longitude/longitude

 Spain
Spain
 Portugal
Portugal