Protection against SSH brutality by means of Iptables
Protection against SSH brutality by means of iptables
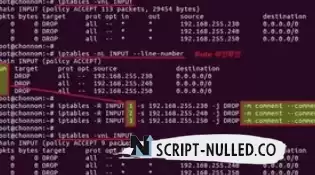
iptables rules can be used to protect against SSH brutality. Executing the rules will block IP addresses that attempt to establish more than the specified number of SH connections in X seconds.
Here is an example of blocking an IP address if more than eight SSH connections are established in 45 seconds:
iptables -A INPUT -p tcp --dport ssh -m conntrack --ctstate NEW -m recent --setiptables -A INPUT -p tcp --dport ssh -m conntrack --ctstate NEW -m recent --update --seconds 45 --hitcount 8 -j DROP
Note that the first command is used to track new connections coming to port 22 (SSH), and the second command instructs iptables to reject packets from an IP address that has sent eight or more requests in 45 seconds.
If you want to insert these two rules at the beginning of the INPUT chain (to activate them before the rest of your rules), use -I instead of -A as the first parameter.
Another good option is to use a whitelist, as this allows you to allow one or more IP addresses to access your server, rejecting everything else.
Here is the command to use this technique:
iptables -I INPUT -p tcp -s 10.10.10.10,192.168.1.14 --dport ssh -j ACCEPTiptables -I INPUT -p tcp --dport ssh -j DROP
SSH connections will be allowed only from these two IP addresses, while any access from any other IP address will be blocked.

 Spain
Spain
 Portugal
Portugal



