Apache Tomcat Security Enhancement Guide
Tomcat is one of the most popular servlet servers and JSP containers. It is used by some of the following high traffic sites:
LinkedIn.com
Dailymail.co.uk
Comcast.net
Wallmart.com
Reuters.com
Meetup.com
Webs.com
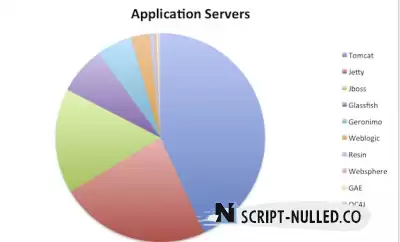
The chart below shows Tomcat's market position on the Java application server.
Technically, you can use Tomcat as an interface server to directly serve site requests. However, in a production environment, you can use some web servers, such as Apache, Nginx, as an interface for routing requests to Tomcat.
Using a web server to process requests improves performance and security. If you are using Apache HTTP as a front-end web server, then you should also consider protecting it.
Tomcat's default setting can reveal sensitive information that helps a hacker prepare for an attack on an application.
1. Delete the Server Banner
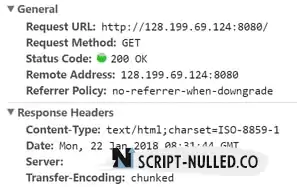
Removing the Server Banner from the HTTP header is one of the first things to do to enhance protection.
The presence of Server Banner information about the product you are using and its version leads to a vulnerability related to information leakage.
By default, the page served by Tomcat will be displayed as follows.
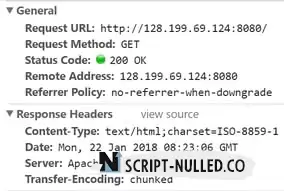
Let's hide the product and version information from the server header.
Go to the $tomcat/conf folder
Change server.xml using vi
Add the following to the Connector port
Server =” “
Example: -
<Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000"
Server =" " redirectPort="8443" />
Save the file and restart Tomcat. Now, when you access the application, you should see an empty value for the server header.
2. Launch Tomcat with Security Manager
Security Manager protects you from an unreliable applet running in your browser.
Running Tomcat with Security Manager is better than without it. Tomcat has excellent documentation on Tomcat Security Manager.
The good thing is that you don't need to change any configuration file. It's just a way of doing it. startup.sh the file.
All you have to do is run tomcat with the –security argument.
bin]# ./startup.sh -securityUsingCATALINA_BASE: /opt/tomcatUsingCATALINA_HOME: /opt/tomcatUsingCATALINA_TMPDIR: /opt/tomcat/tempUsingJRE_HOME: /usrUsingCLASSPATH: /opt/tomcat/bin/bootstrap.jar:/opt/tomcat/bin/tomcat-juli.jarUsingSecurity ManagerTomcatstarted.bin]#
3. Enable SSL/TLS
Serving web requests over HTTPS is essential to protect data between the client and Tomcat. To make your web application accessible via HTTPS, you need to implement an SSL certificate.
Assuming that you already have a ready-made keystore with a certificate, you can add the following line to the server. The XML file is in the Connector port section.
SSLEnabled="true" scheme="https" keystoreFile="ssl/bloggerflare.jks" keystorePass="chandan" clientAuth="false" sslProtocol="TLS"
Change the Keystore file name and password to your own.
4. Apply HTTPS
This applies only when you have enabled SSL. If not, it will break the app.
Once you have enabled SSL, it would be good to force redirect all HTTP requests to HTTPS for secure communication between the user and the Tomcat application server.
Go to the $tomcat/conf folder
Change the web.xml using vi
Add the following before the </web-app> syntax
<security-constraint><web-resource-collection><web-resource-name>Protected Context</web-resource-name><url-pattern>/*</url-pattern></web-resource-collection><user-data-constraint><transport-guarantee>CONFIDENTIAL</transport-guarantee></user-data-constraint></security-constraint>
Save the file and restart Tomcat.
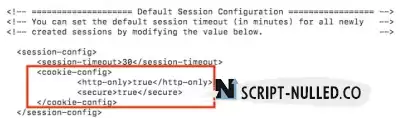
5. Add the Secure & HttpOnly flag to the Cookie
It is possible to steal or manipulate the web application session and cookies without using a secure cookie. This is the flag that is entered in the response header.
This is done by adding the following line to the session-config section of the file web.xml
<cookie-config><http-only>true</http-only><secure>true</secure></cookie-config>
Screenshot of the configuration:
Save the file and restart Tomcat to check the HTTP response header.
6. Launch Tomcat from an unprivileged account
It is good to use a separate unprivileged user for Tomcat. The idea here is to protect other services running in case any account is hacked.
Create a UNIX user, say tomcat
useraddtomcat
Stop Tomcat if it is running
Change the $tomcat affiliation to the tomcat user
chown-R tomcat:tomcat tomcat/
Launch Tomcat and make sure it works with the Tomcat user
7. Remove standard/unwanted applications
By default, Tomcat comes with the following web applications that are not required in a production environment.
You can delete them to avoid any unknown security threat with the default Tomcat application.
ROOT is the default welcome page
Docs - Tomcat documentation
Examples - JSP and servlets for demonstration
Manager, host-manager - Tomcat administration
They are available in the $tomcat/webapps folder
[root@itgap webapps]# ls-ltdrwxr-xr-x14tomcattomcat4096Sep2915:26docsdrwxr-xr-x7tomcattomcat4096Sep2915:26examplesdrwxr-xr-x5tomcattomcat4096Sep2915:26host-managerdrwxr-xr-x5tomcattomcat4096Sep2915:26managerdrwxr-xr-x3tomcattomcat4096Sep2915:26ROOT[root@itgap webapps]#
8. Change the port and shutdown command
By default, tomcat is configured to disconnect on port 8005.
Did you know that you can disable a tomcat instance by running the telnet command in IP:port and running the SHUTDOWN command?
Chandans# telnet localhost 8005Trying ::1... telnet:connectto address ::1:Connectionrefused Trying 127.0.0.1...Connectedto localhost.Escapecharacter is '^]'.SHUTDOWNConnection closed by foreign host.Chandans#
You see, having a default configuration leads to a high security risk.
It is recommended to change the tomcat shutdown port and the default command to something unpredictable.
Change the following in server.xml
<Serverport="8005"shutdown="SHUTDOWN">
8005 - Change to another unused port
SHUTDOWN - change to something complicated
For example:
<Serverport="8867"shutdown="NOTGONNAGUESS">
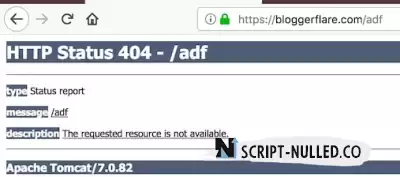
9. Replace the default 404, 403, 500 pages
The presence of a default page for not found, prohibited, server errors reveals the details of the version.
Let's look at the default 404 page.
You can first create a page with a common error and configure web.xml to redirect to a page with a common error.
Go to the $tomcat/webapps/$ application
Create an error file.jsp using the vi editor
<html><head><title> Error Page </ title></ head><body> eror! </ body></ html>
Go to the $tomcat/conf folder
Add the following to the file web.xml . Make sure that you have added before <web-app/>
<error-page><error-code>404</error-code><location>/error.jsp</location></error-page><error-page><error-code>403</error-code><location>/error.jsp</location></error-page><error-page><error-code>500</error-code><location>/error.jsp</location></error-page>
Restart the Tomcat server to test it
Much better!
You can do this also in java.lang.Exception. This will help not to disclose information about the tomcat version if there is a java lang exception.
Just add the following web.xml and restart the Tomcat server.
<error-page><exception-type>java.lang.Exception</exception-type><location>/error.jsp</location></error-page>
I hope that the above guide will give you an idea of Tomcat security.

 Spain
Spain
 Portugal
Portugal