💬 true story... How I was hacked, my cryptocurrency wallets were emptied, and what Apple said.

• The story of how the creator of the website for job search in the field of cryptocurrencies cryptojobslist withdrew personal savings in cryptocurrency, simultaneously gaining access to Apple, Yahoo, Gmail and Telegram accounts with two-factor authentication enabled.
I was hacked. The attacker gained access to several accounts (Apple Cloud, Yahoo, Gmail, Telegram), found private keys, a mnemonic phrase and stole a cryptocurrency worth several thousand dollars.
In this article, I will try to recreate the exact chronology of events, calculate the damage, and comment on how this could have happened. I will also tell you about a few points that I haven't quite figured out yet (mainly in the field of 2FA), I hope that my readers will be able to help me. I will also share a few tips on what you can do today to protect yourself from attacks like the one that happened to me.
Chronology of the attack
The events took place on Sunday morning, October 4, 2020. In the interval from 9 to 11 am, GMT +8. I was not at home, I was far away from my two MacBooks. They were locked, closed, and in hibernation mode. The night before, I finished setting up my new MacBook Pro (2020).
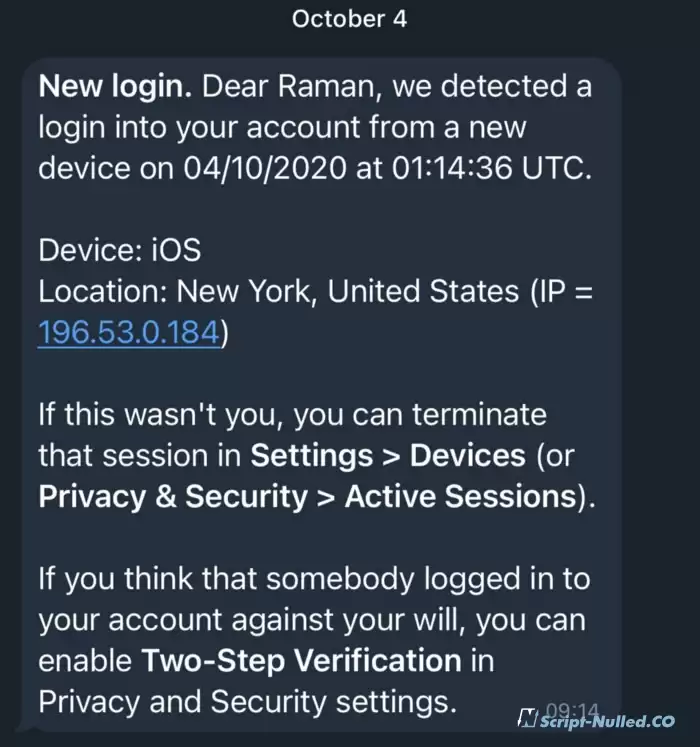
This one is new (certified, not used by anyone before, taken from the official Apple store) I received the MacBook on Friday (October 2). Saturday ~ 20:00. I've finished the setup. Sunday, ~ 9:14, the attack has begun. I suddenly started receiving SMS notifications with confirmation codes to log in to accounts on my phone.
9:14 - I get a notification about a new login to my Telegram. Before that, I did not receive codes from Telegram via SMS or chat history. (Did the attacker delete the code? Telegram does not send you an SMS if you are logged in to your account on multiple devices, instead it sends a code in the app.)
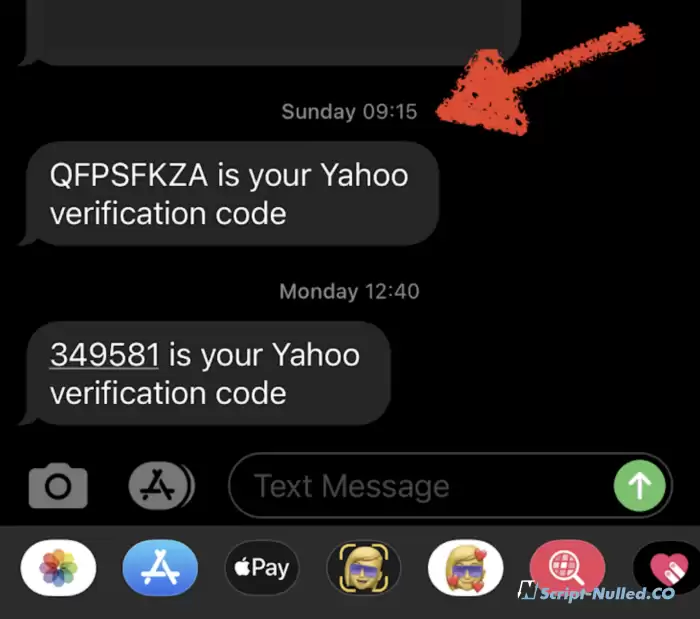
9:15 - Confirmation code from Yahoo. Again, I didn't request:
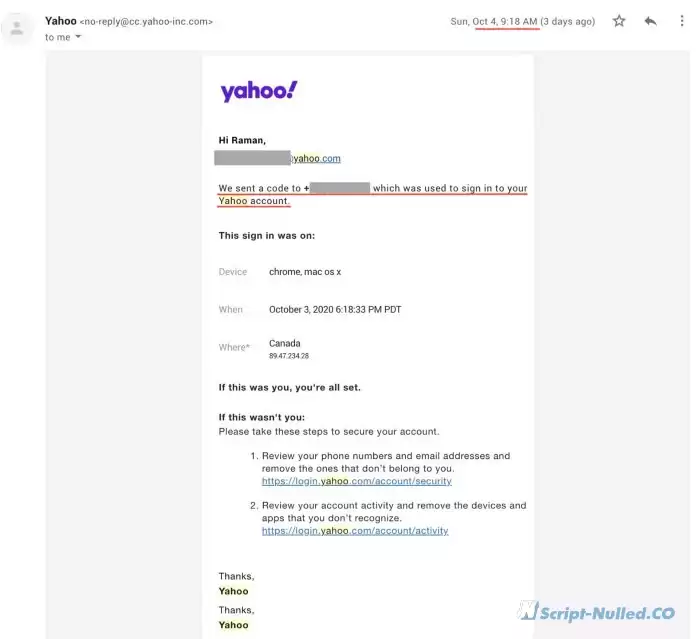
9.18 - Immediately after this code, I received an email notification of a password change request. "We have sent a code to the <phone number> that was used to log in to your Yahoo account":
9.18 - password changed:

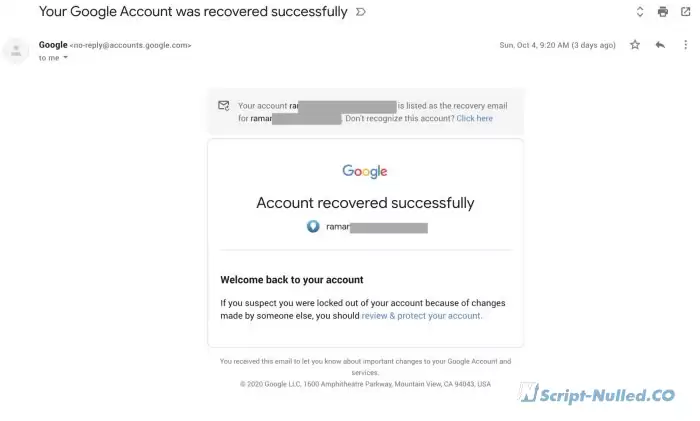
9.20 - login to the old Gmail account (Google Apps).

The attacker synced his Google Chrome with my account. This means that all the passwords that were stored in the Google Password Manager for this account have leaked. Chrome also allows you to export them to CSV. I assume that the attacker used exactly this function. The exported passwords were used as a dictionary in the next stages of the attack.
9:28 - call from Apple. I pick up the phone. The robot's voice reads out the confirmation code, and the line is cut off.
9.29 - I receive an email about successfully logging in to my Apple ID:
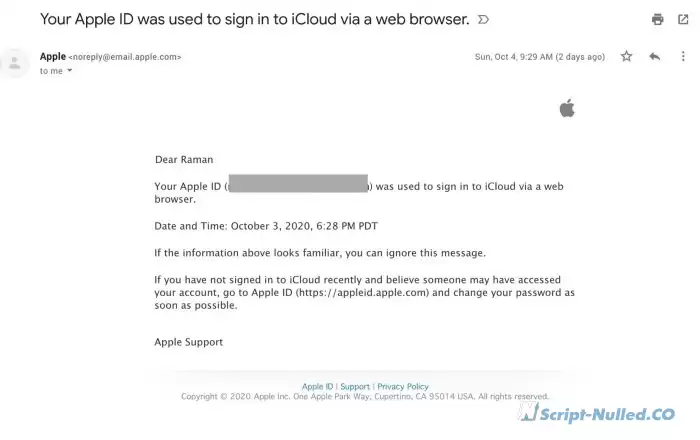
By 9.40 I got home. Stress was off the scale + sweat is running like a stream. I open my laptops, trying to figure out what's going on. I'm starting to change passwords. When suddenly:
10:09. I receive notifications about the movement of tokens from one of my wallets.
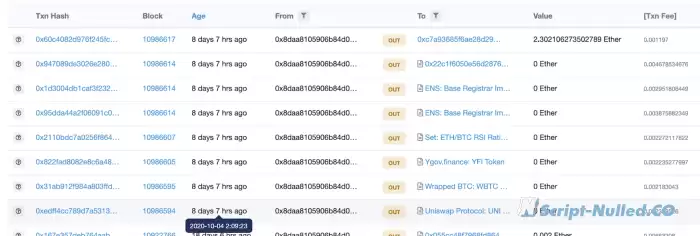
These wallets have withdrawn my money:
0xc7a93685f6ae28d29d4a6e974a9c774f8ebbc904
0x8C46335777867367e279350eEDacdA5463de9029
Several unauthorized transactions, draining tokens and cryptocurrencies:
0x60c4082d976f245fc3c2ff52814cea5858a89423f7f81046da45809a5d0f37a1
0x31ab912f984a803ffd4e79340e050a31254535f07050242eb72dd360fce4a851
0xedff4cc789d7a53133a4451680f1e73321c52b5da1725432a4288ac4e418c356
0x929226416c83da6a4a2962368803c392b2d05b701aad419269b032e1a125c411
0x542e3f237013bd7e81b5b90fffc5c83aa46824a38e9fd535a533d5f00dddfaef
0x4a370b66e5ea3577dfe9fce2230fefda0d27de1cf913d9215953a534352652ae
The hacker withdrew ~ 800 ETH, ~ 1700 dollars earned by blood and sweat UNI, ~ 209.73 dollars ETH / BTC RSI, ~ 40 dollars WBTC, 27 DAI, etc. for a total of $ 3000 ++
I'm not stressed anymore. I'm shaking.
There were several old hot wallets stored in my iCloud. Some are in the form of a file. Some of them were protected by a password that was recorded in Apple Notes. I quickly realized that the problem had reached a whole new level. And after a few seconds, I also realized that I had to start withdrawing funds from all wallets that are linked to my iCloud. The transfer of cryptocurrency itself causes stress - there is always a risk of sending money to the wrong address and losing it forever. Performing transfers under pressure, when every second counts, is already the next level. I did my best. "Can I transfer all tokens first? Or the whole broadcast? What is more valuable? What will a hacker do first? " - a thousand thoughts rush through my head.
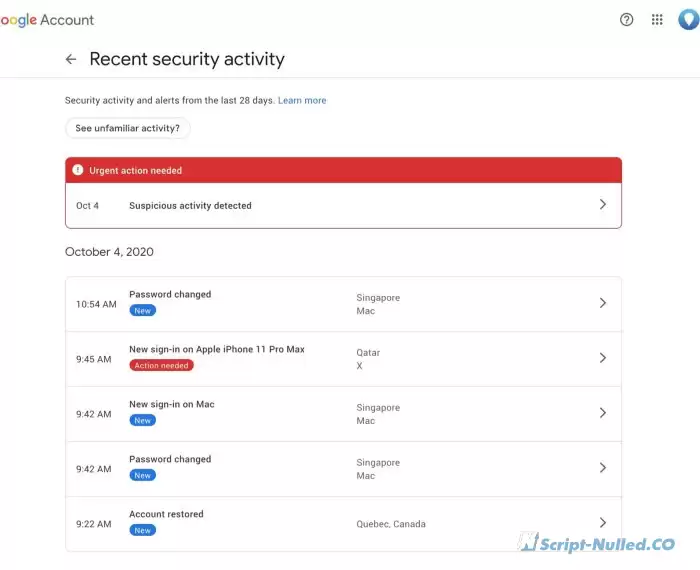
Tuesday. I'm trying to figure out what happened. In case someone physically gained access to my laptops, I decided to look at the logs.
pmset -g log | grep -e “ Sleep “ -e “ Wake “
This allowed me to find out what was happening when both computers were turned on and off.
I didn't notice any activity during the hours when I was hacked. My laptops were asleep. The lids were closed. I remember a little battery activity, but I don't see anything unusual about it. Most Mac computers wake up for a few seconds or ms to perform their standard maintenance actions.
Wednesday evening - my old laptop was running a little slow (as usual) and I decided to reboot it. When it started to boot, it went into "Install" mode. This happens when a major OS X update arrives on the Mac. I don't remember any new versions of OS X coming out or any updates waiting to be installed... naturally, I had my suspicions. I thought that given the recent hack, it's better not to take any chances. The last thing I need is some malware to format my hard drive. So I forcibly shut down my Mac. And the next day I took it to the Apple Store.
Thursday - went to the Apple Store. I was very surprised that no one at Apple seems to understand how to work with the CLI after restarting the computer. The genius who helped me said that I was more knowledgeable than him after 10 minutes of conversation. (Although he was very nice.) We rebooted the machine using an external hard drive. I have moved files that are dear to me. And we started restarting my laptop again. After about 20 minutes, it finally started. Nothing was formatted. I was happy... for a moment.
Apple Genius managed to find a more expensive Senior Genius and tell him this case. By an incredible coincidence, this guy had a background in cyber forensics. However, the rules of the Apple retail store did not allow him to share his opinion or interact with my machines beyond the basic level of "let's reinstall the OS".
Conclusions and mistakes to avoid:
If you store private keys or mnemonics in Apple Notes or iCloud, outsiders can access them. Even if you have 2FA installed. Even if your notes are password protected. Use a hardware wallet for everything, no matter how much cryptocurrency you store.
Install 2FA in Telegram right now if you haven't done it yet. If your Telegram is hacked and you don't have a password, hackers will install it for you. And the only way to reset it is to reset the entire account.
Make sure that you don't use the password twice, three times, etc. anywhere, even partially. Create unique passwords for each service you sign up for. Save them in the password manager. Do not store your primary email address in the password manager. Remember the main master passwords and do not use them again.
Don't save passwords in Chrome. Or, if you still can't opt out of it, make sure that your Google account has several levels of 2FA protection. SMS is not included in this list.
iCloud has limited security capabilities. Consider using a Google Voice number as a 2FA.
When you leave your laptop unattended or close it at night, be sure to turn off Wi-Fi. Or, even better, turn it off completely. It is not enough to close the lid and switch to hibernation mode. Your laptop can wake up at any moment to execute the code remotely, even if the lid is closed.
More screenshots

 Spain
Spain
 Portugal
Portugal





