How to protect yourself from DDoS attacks?
How to protect yourself from DDoS attacks, what steps to take? First of all, it is not necessary to postpone it "for later". Some measures should be taken into account when configuring the network, starting servers and deploying software. And each subsequent change should not increase vulnerability from DDoS attacks.
Security of the program code. When writing software, security considerations should be taken into account. It is recommended to follow the standards of "secure coding" and thoroughly test the software to avoid common errors and vulnerabilities, such as cross-site scripts and SQL injections.
Develop an action plan when updating the software. There should always be the possibility of a "rollback" in case something goes wrong.
Update the software in a timely manner. If it was possible to roll out updates, but there were problems, see point 2.
Do not forget about access restrictions. Admin and/or accounts must be protected by strong and regularly changed passwords. It is also necessary to periodically audit access rights, timely deletion of accounts of retired employees.
The admin interface should be accessible only from the internal network or via VPN. Close VPN access in a timely manner for dismissed and even more so dismissed employees.
Include the elimination of the consequences of DDoS attacks in the disaster recovery plan. The plan should include ways to identify the fact of such an attack, contacts for communication with an Internet or hosting provider, a "problem escalation" tree for each department.
Scanning for vulnerabilities will help identify problems in your infrastructure and software, and reduce risks. A simple OWASP Top 10 Vulnerability test will identify the most critical problems. Penetration tests will also be useful – they will help to find weaknesses.
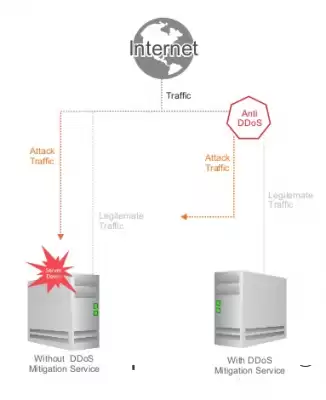
Hardware protection against DDoS attacks can be expensive. If your budget does not provide for this, then there is a good alternative - DDoS protection "on demand". Such a service can be enabled by simply changing the traffic routing scheme in an emergency, or it is constantly protected.
Use a CDN partner. Content Delivery Networks (Content Delivery Network) allow you to deliver site content via a distributed network. Traffic is distributed across a variety of servers, reducing the latency when accessing users, including geographically remote ones. Thus, although the main advantage of CDN is speed, it also serves as a barrier between the main server and users.
Use Web Application Firewall - a firewall for web applications. It monitors the traffic between the site or application and the browser, checking the legitimacy of requests. Working at the application level, WAF can detect attacks on stored patterns and detect unusual behavior. Application-level attacks are not uncommon in e-commerce. As in the case of CDN, you can use WAF services in the cloud. However, configuring the rules requires some experience. Ideally, all major applications should be provided with WAF protection.
DNS protection
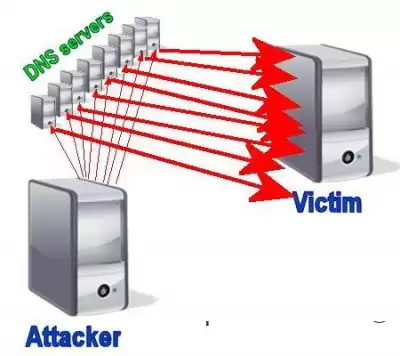
And how to protect the DNS infrastructure from DDoS attacks? Conventional firewalls and IPS will not help here, they are powerless against a complex DDoS attack on DNS. In fact, firewalls and intrusion prevention systems are themselves vulnerable to DDoS attacks.
Cloud services for cleaning traffic can come to the rescue: it is sent to a certain center, where it is checked and redirected back to its destination. These services are useful for TCP traffic. Those who manage their DNS infrastructure themselves can take the following measures to mitigate the consequences of DDoS attacks.
Monitoring DNS servers for suspicious activity is the first step in protecting the DNS infrastructure. Commercial DNS solutions and open source products such as BIND provide real-time statistics that can be used to detect DDoS attacks. Monitoring DDoS attacks can be a resource-intensive task. It is best to create a basic infrastructure profile under normal operating conditions and then update it from time to time as the infrastructure develops and traffic patterns change.
Additional DNS server resources will help to cope with small-scale attacks due to redundancy of the DNS infrastructure. Server resources and network resources should not be enough to handle a larger volume of requests. Of course, redundancy costs money. You pay for server and network resources that are not normally used under normal conditions. And with a significant "reserve" of power, this approach is unlikely to be effective.
Enabling DNS Response Rate Limiting (RRL) will reduce the likelihood that the server will be involved in a DDoS Reflection attack – the speed of its response to repeated requests will decrease. Many DNS implementations support RRL.
Use high availability configurations. You can protect yourself from DDoS attacks by deploying a DNS service on a high availability (HA) server. If one physical server "crashes" as a result of the attack, the DNS service can be restored on the backup server.
The best way to protect DNS from DDoS attacks is to use a geographically distributed Anycast network. Distributed DNS networks can be implemented using two different approaches: Unicast or Anycast addressing. The first approach is much easier to implement, but the second is much more resistant to DDoS attacks.
In the case of Unicast, each of your company's DNS servers receives a unique IP address. DNS maintains a table of your domain's DNS servers and corresponding IP addresses. When a user enters a URL, one of the IP addresses is randomly selected to execute the request.
In the Anycast addressing scheme, different DNS servers use a common IP address. When the user enters the URL, the collective address of the DNS servers is returned. The IP network routes the request to the nearest server.
Anycast provides fundamental advantages over Unicast in terms of security. Unicast provides the IP addresses of individual servers, so attackers can initiate targeted attacks on certain physical servers and virtual machines, and when the resources of this system are exhausted, the service fails. Anycast can help mitigate DDoS attacks by distributing requests between a group of servers. Anycast is also useful to use to isolate the effects of an attack.
Means of protection against DDoS attacks provided by the provider
Designing, deploying and operating a global Anycast network requires time, money and know-how. Most IT organizations do not have the specialists and finances for this. You can entrust the functioning of the DNS infrastructure to a provider - a provider of managed services that specializes in DNS. They have the necessary knowledge to protect DNS from DDoS attacks.
Managed DNS service providers operate large-scale Anycast networks and have points of presence around the world. Network security experts monitor the network 24/7/365 and use special tools to mitigate the consequences of DDoS attacks.
DDoS protection services are also offered by some hosting service providers: network traffic analysis is performed 24/7, so your site will be relatively safe. Such protection is able to withstand powerful attacks - up to 1500 Gbit/sec. The traffic is paid at the same time.
Another option is IP address protection. The provider places the IP address that the client has chosen as the protected one into a special network analyzer. During an attack, traffic to the client is mapped to known attack patterns. As a result, the client receives only pure, filtered traffic. Thus, users of the site may not find out that an attack was launched on it. To organize this, a distributed network of filtering nodes is created so that for each attack it is possible to select the closest node and minimize the delay in traffic transmission.
The result of using DDoS protection services will be timely detection and prevention of DDoS attacks, the continuity of the functioning of the site and its constant availability to users, minimizing financial and reputational losses from downtime of the site or portal.

 Spain
Spain
 Portugal
Portugal