How to achieve maximum anonymity from a laptop or computer
The fact that we are being monitored every day is no secret to anyone, and your correspondence from VK or search queries will be given at the first request of law enforcement agencies. I am the one who was directly affected by this topic.
Today I will teach you how to anonymize your traffic and location as much as possible while sitting at your workplace.
I am not encouraging you to illegal actions, this manual and all subsequent ones are just a review of tools for certain needs.
There are many vulnerabilities that will help you find and your human factor plays an important role.
Do not think that after doing all the actions you will be 100% safe and confidential
Launching Whonix-Gateway-XFCE.
As a rule, they are installed already with optimal settings, so you can start immediately. First we launch Gateway, then Workstation.
At the first start, in both systems, a window will appear in front of us in which we select "Understanding” and click "Next", in the second window that appears, we repeat the same, the inscription “Whonix Setup is completed" will appear, after which we can press "Finish".
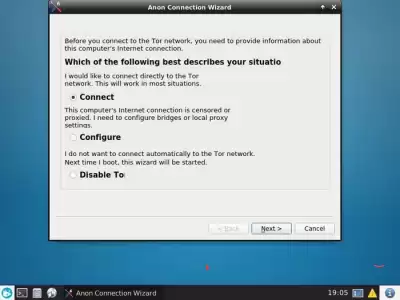
The “Anon Connection Wizard" window will appear on the Gateway, select "Connect” and click "Next” and then "Finish.”
We are starting with Kali Linux, we will not have the Internet yet, since Tor traffic is sent through the gateway, and we have not yet taught Kali to accept it.
Disconnect the network adapter:
sudo ip link set eth0 down
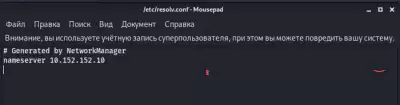
Editing the file:
sudo mousepad /etc/resolv.conf
We delete everything in it and change it to
nameserver 10.152.152.10
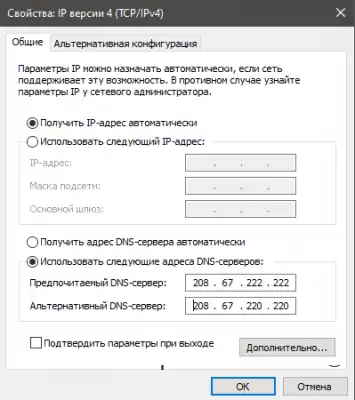
Step 3. Provider (DNS-Leak)
The fact is that the provider sees how we access the Internet through the tor network.
In order to avoid wiretapping of our traffic by the provider, we need to encrypt or hide it.
The easiest option is to change our DNS.
There are still ways to hide from the provider, there is a tool "dns crypt" you can find it on the Internet, but I did not use it.
Step 4. WebRTC
Browsers have a built-in WebRTC function, it is needed in some applications to use p2p, it allows you to connect 2 clients directly to each other, this vulnerability can be used to reveal your real IP address even if you use a VPN.
Step 4. Additional
On your Host machine, you can use a VPN only if you trust it 100% and never pay for such services from your card and your IP
If you have something to add, you can write and suggest it to me, I will be happy to discuss any interesting information.

 Spain
Spain
 Portugal
Portugal