The final version of Invision Community 4.3.0 has become available - commercial software for organizing web forums developed by the American company Invision Power Services Inc.
Some new features of Invision Community 4.3.

The final version of Invision Community 4.3.0 has become available - commercial software for organizing web forums developed by the American company Invision Power Services Inc.
Some new features of Invision Community 4.3.

IPS Community Suite 4.3.1 NULLED is a new release of the IPS Forum line featuring numerous improvements and several new features. Version 4.3.1 is a minor maintenance update that fixes the issues described with 4.3.0.
** IMPORTANT NOTIFICATION **
Please note that not all third-party applications and themes are still compatible with Invision Community 4.3. If you use third-party resources, including custom themes, make sure that they have been declared compatible by their authors or as a result your site may not be functional after the update.

IPS Community Suite 4.3.2 NULLED is a new release of the IPS forum line, which presents numerous improvements and several new features. Version 4.3.2 is a minor maintenance update that fixes the issues described with 4.3.1.

IPS Community Suite 4.3.3 NULLED is a new release of the IPS forum line, which presents numerous improvements and several new features, as well as GDPR support. Version 4.3.3 is a minor maintenance update that fixes the issues described with 4.3.2.
Changes:
- New opportunities for GDPR compliance:
- A new feature for administrators to upload an XML file of all personal information.
- New setting for automatic pruning of IP address records.
- A new option when deleting a participant for anonymous content submitted by them.
- New setting to automatically add links to privacy policies of integrated third-party services such as Google Analytics or Facebook Pixel to your privacy policy, if they are enabled.
- Fixes an issue where calendar events presented in different time zones to the user may be displayed at the wrong time.
- Other minor bug fixes and improvements.

IPS Community Suite 4.3.4 NULLED is a new release of the IPS forum line in which a filter has been added to view participants who have an option for mass mailing in ACP, and the ability to opt out of these participants and fix errors. Version 4.3.4 is a minor maintenance update that fixes the issues described with 4.3.3.

IPS Community Suite 4.3.5 NULLED - version 4.3.5 which is a small update for maintenance and fixing problems reported since 4.3.4.

Commercial software for organizing web forums developed by the American company Invision Power Services Inc. It is written entirely in PHP, mainly uses MySQL as a database, but there is also support for Microsoft SQL Server

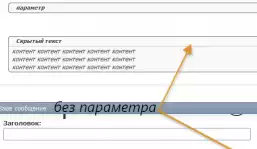
Name: VSQ - Spoiler
Description: The spoiler tag allows you to hide large texts, codes, images, etc. This hack is partially based on the DI - BBCode spoiler hack from diSmiSS
Title: QuickQuote (Quick quote, Quick quote)
Version: 1.4.2
Author: MDM
vB versions: 4.0.x
Encoding: CP1251, UTF-8
Description: Inserting a quote and a user's nickname into a quick response form.
Post Thanks - gratitude system
hack rewritten from line 3.8 to line 4.0.0
vBulletin Integration Module 1.07 - This module allows you to integrate SocialEngine with the well-known and popular vBulletin forum engine in such a way that two different platforms will work as a single system.
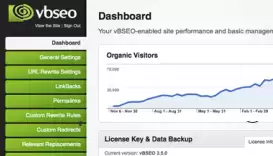
vBSEO 3.5.2 is a plugin for search engine optimization of forums built on the vBulletin 3.x.x - 4.0.x system. vBSEO is easily installed on the forum and the entire installation process takes 1-5 minutes. The setup takes a little longer. The module has a powerful "Settings Panel" in its system.
vBSEO 3.5.2 plugin - optimizes your forum in real time, allowing Google and other search engines to find all the information on your forum pages, index them, and rank them in a number of key ones as they are prioritized.


| « July 2025 » | ||||||
|---|---|---|---|---|---|---|
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||