Chat 2 by Siropu is an AJAX chat plugin for XenForo 2. In the latest update, previously stated chat and style errors have been fixed.
Chat 2 by Siropu is an AJAX chat plugin for XenForo 2. In the latest update, previously stated chat and style errors have been fixed.

User Mentions Improvements is an advanced system for mentioning XenForo 2 users.

Have you ever come across a situation where you want to create a topic prefix with multiple tags? Now with the help of the Multi Prefix plugin you can do it. All the same functions work, pressing the prefix shows all the topics with the prefix. Searching for a prefix will show all topics containing this prefix (plus others). Supported content types: themes, resources.

The filter gives your visitors the ability to easily navigate to the desired content - without updating - using the filter widget or filter panel to upload results directly to the page they are on, without waiting for the page to load.
[SVG] Messengers is a XenForo 2 plugin that adds icons of messengers and social networks with information in the XenForo 2 postbit

Adds a custom footer block. Based on the style of a Turkish developer and redesigned in detail.
Implemented:
Flexible style settings
Setting up the footer
This add-on adds the traditional reputation feature to XenForo 2. With this add-on, users can give reputation points to other users in the same way they can use reactions.
The addon creates a live forum statistics widget to keep your users up to date. The displayed data is current and can be updated at any time, it includes user and thread statistics, as well as a list of new threads.
Information:
Besides being a statistical widget, it allows you to sell attached posts to monetize your forum. Using this add-on, you can sell links to custom themes and external links inside the widget.
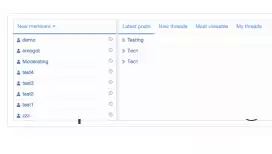
Paygate: Yandex.Money - this modification allows you to set up payment acceptance on your forum via Yandex.Money.
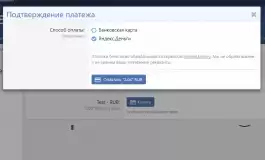
Nixfifty Tickets is a plugin for the XenForo 2 support system designed to combine all your support needs into one easy-to-use solution.
DragonByte eCommerce is a high-tech online store plugin for XenForo 2, containing advanced features such as multiple price levels, coupons and automatic sales. Fully integrated with XenForo 2, DragonByte eCommerce uses all the built-in features of XenForo 2, such as a new payment profile system that allows you to accept payments from different payment systems.
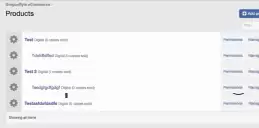
Based on the merged DUMPz.ws pulled TeslaCloud developer plugins from this dump

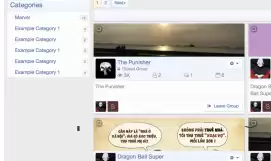
Social Groups is a complete social group system for the XenForo 2 forum with excellent features and a friendly interface.
It has interesting features and excellent code quality. It was developed after careful research to meet the requirements of people interested in creating custom catalogs. The design is modern, but at the same time it focuses on usability, visual hierarchy and aesthetics to provide easy navigation for end users. With Ryzer Pro, you will have both light and dark versions. So you get two themes.
Set up your forum
XF2 Essential Suite offers everything you need to take your forum to the next level, regardless of whether you are a small or large player.
Collection of add-ons and themes
Thanks to XenForo 2's extensive list of add-ons and themes, you'll have the tools you need when you need them.
Save money with XF2 Essential Suite
A set of our XF2 products on a single copy of XenForo at a quarterly or annual price. We are sure that you will like our products and price!
Free removal of brands
Remove branding from add-ons and themes.



