POSGo SaaS is an efficient point of sales tool for the management of sales and purchases. It facilitates the achievement of sales targets in multiple branches through easy monitoring. This tool is easy to use and effective for organizations of varied sizes. With a SaaS version, create plans using a Super Admin Login.

Start a business with this Contactless Restaurant Menu Maker within 5 minutes. With the help of this digital menu, customers can scan the QR code and check the menu on their phones.

Elite Quiz Web Version is NOT an independent system. This is available only for esisting customers of Elite Quiz Flutter App Version.

PressFly allows your users to write articles so they and you can earn money by getting paid per article view. PressFly includes a complete system for writing articles, publications, topics, news and posts. Also, it includes referrals system, withdrawal system with the ability to add unlimited withdrawal methods, Login with social networks like Facebook, Twitter & Google, translation ready, multiple captcha integrations like reCAPTCHA v2 Checkbox/invisible and Solve Media and much more!. The inspirational websites like buzzfeed.com, thenextweb.com, makeuseof.com, techcrunch.com, cracked.com, medium.com, whatculture.com, listverse.com & sportskeeda.com
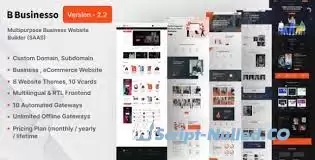
“Businesso” is a Business / Ecommerce Website Builder SAAS (Multitenancy). You can use Businesso to build business / ecommerce website builder within minutes. The business website frontend is Multi-lingual & also RTL supported You can create unlimited monthly / yearly / lifetime packages, control features for that packages. You can make a package Free, Trial, Premium or only free or only trial or only premium. You can set trial days for trial packages.
Master your universe. Nova is a beautifully-designed administration panel for Laravel. Carefully crafted by the creators of Laravel, Nova is designed to make you the most productive developer in the galaxy.

Smart POS is a beautifully crafted Point Of Sale application. The application is packed with a ton of features like Point Of Sale, Invoicing, Quotations, Purchase Orders, Inventory Management, Customer Management, Supplier management, Project Management, Accounts, Data & Reports, REST API, CRON JOBS, Employee Management with distinct user roles. It has options for all types of tax, like Exclusive, Inclusive and GST.

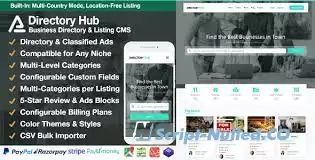
Directory Hub is a business directory PHP script, inspired by Yelp and Yellow Pages, integrated classified ads module, offers features like csv bulk importer, multiple-countries support, unlimited-level categories, custom fields, listing with multiple categories, business listings, and products listings, which give buyers the maximum ability to make any type of business or niche directory website.
Nazmart – Multi-Tenancy eCommerce Website Builder SaaS PHP Scripts. It use Separate Database for each Tenants, so that your website load fast, has option to add custom domains. automatic subdomain creations and much more. it comes with a different 2 theme with necessary inner pages, it will help your tenant to eCommerce website easily without hassle or thinking much about design. it also has 20+ payment gateway, will more than 150currency support. It’s highly customisable, it comes with many awesome features, like drag & drop menu builder, drag & drop form builder, drag & drop widget builder and many more. it’s compatible with Desktop, laptop, mobile and also compatible with major browsers.
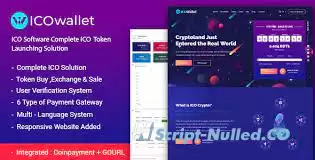
ICOWallet is the Complete Initial Coin offering Software for your CryptoCurrency Business. It has Token initialization and 6 Types of Payment gateways including Coin payment and GOURL. Here you can do any types of Coin offering services and You can Sell the Package to your Customers and will take investment from users.
With MailWizz not only that you will be able to properly handle email marketing for your own purposes but you can also become an Email Service Provider for your customers, since MailWizz integrates easily with payment gateways like Paypal and it offers all the needed tools to create pricing plans, promotional codes and to manage orders and transactions created by your customers.

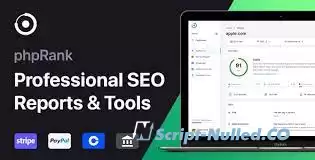
phpRank is a comprehensive SEO Report Platform, that allows you to generate insightful, concise and easy to understand SEO reports that will help your webpage rank and perform better.
phpAnalytics is a privacy focused, web analytics software solution. It provides detailed web traffic reports, such as Realtime, Overview, Acquisitions, Behavior, Geographic, Technology, Events, and more.
Upload your logo, select custom colors, select a pattern and download the final QRcode. Available formats: .png, .svg.

OTT platforms are a growing industry and day by day on-demand movie streaming platforms are getting popular. Video Streaming Portal that enables a great opportunity to create your video streaming website. No need to pay thousands of dollars to hire developers to build your video streaming Website. Video Streaming Portal is to develop your entertainment networks such as movies, shows, sports and live tv.






 Spain
Spain
 Portugal
Portugal













