Dashboard Helpful overview of open projects, open invoices, received and outstanding payments, open tasks, messages and events. Project Management Create and manage all your projects. Project Tasks You can add tasks to any project. Support Tickets Let your Clients open tickets to keep track of any incident. It also supports email tickets. Project Timer This will help you to track the time you have spent on a project.
Elitepack CSS3 Pricing Tables and boxes are a collection of pure CSS3 Pricing web elements that are uniquely designed to showcase pricing features for your products or services.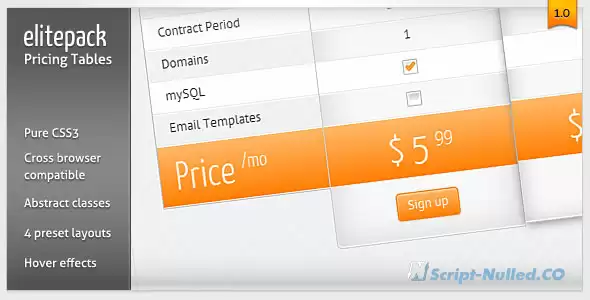
Easy Video Background lets you add video in the background of your website with a single jаvascript call. The script automatically picks the most optimal video format based on the browser where it is being run in. Furthermore it has a built in image fallback for mobile devices where it is not possible to have video playing as a background. When the HTML5 video tag is not supported, a Flash fallback will make sure the video will be visible.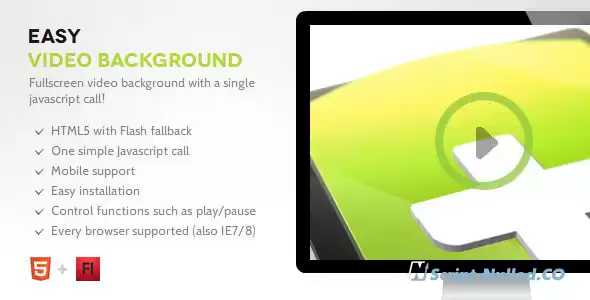
You have a wonderful WooCommerce Shop and you want to show it to your offline customers? Then this plugin will fulfill your needs: Create a PDF Catalog from your whole Shop or just from a product category. Directly inside your shop, customizable as you want and simply beautiful! No need of HTML or CSS, create everything inside the admin panel.
User Registration plugin provides you with an easy way to create frontend user registration form and login form. Drag and Drop fields make ordering and creating forms extremely easy. The plugin is lightweight, extendible, and can be used to create any type of registration form.
Plugin allows you to manage reservations for your restaurant business. This plugin can help to receive reservations from clients online. Your clients will be able to see available space at specified time, and if it’s available, client is able to make a table reservation. Initially you need to setup number of persons that can book at one time, working times and restaurant details. Plugin automatically detects free seats and if available reservation is instantly confirmed. There is a possibility to control every incoming reservation as well in manual mode.
Maika is an advanced gallery plugin to show gallery and more your work. Maika compatible with visual composer, WPML . You can change all colors, font sizes, image size, spacings etc. from powerful shortcode and plugins settings panel.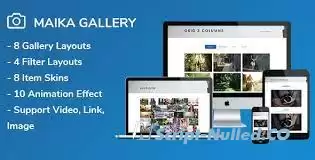
LearnPress WordPress LMS PRO Bundle is a series of premium LearnPress’s Add-ons. With this LearnPress PRO Bundle, you will get both the unlimited power of LearnPress – LMS WordPress Plugin with most of its Premium Add-ons and the beautiful out-of-the-box design to quickly build your online course website.
WordPress white label branding, maintenance mode and coming soon landing pages, and all the rebranding WordPress can handle. WordPress branding is all over your login page, dashboard, system emails, footers, menus and code. Branda Pro is the smoothest WordPress branding plugin for white labeling your CMS.
WP ULike: The Best WordPress Marketing Automation The WordPress Leading Marketing Plugin A professional WordPress plugin that makes your website more attractive and user-friendly.
The Simplest Way to Implement Schema Markup Boost your website SEO in a few clicks. No coding skills needed.
Stackable lets you experience the power of page builders inside Gutenberg, with stunning customizable blocks and hundreds of pre-made designs.
WPCode (formerly known as Insert Headers and Footers by WPBeginner) is the most popular code snippets plugin for WordPress used by over 1 million websites. WPCode makes it easy and safe to add custom WordPress features through code snippets, so you can reduce the number of plugins on your site.
Site Search
Site Menu
☑ Websites Scripts
Recent comments

Survey on the website
Evaluate the work of the site
Tag Cloud
Popular
Statistics
- +8 Total articles 7411
- +22 Comments 5098
- +25 Users : 7483

 Spain
Spain
 Portugal
Portugal