March
23
2023
Introducing DallHam, an innovative platform powered by OpenAI that combines the intelligence of ChatGPT and Dalle to provide a powerful SAAS system. With DallHam AI, you can access multiple options including a text with an image generator and the ability to generate content for a variety of needs by simply giving a text hint to the AI.


March
23
2023
Nexelit Multipurpose Website & Agency Business CMS is the perfect agency business or any kind of website with this PHP Script. Nexelit is a better way to present your business, corporate website, construction website, interior, agency, events, event ticket selling, donation website, crowdfunding, fund rising, job posting, manage your customer, quotation, clients feedback, product selling, digital product selling, physical product selling, downloadable product selling, various kind of website etc. It’s easy to customise and also well documented. it also compatible with Desktop, laptop, mobile and also compatible with major browsers.


March
23
2023
PhpContent is an AI Content Generator Platform, that allows you create unique and engaging content, that will increase conversions and drive sales, and generate stunning images that will increase engagement.

March
23
2023
SurveyClick is a PHP survey builder script. The multitude of options allows you to create the most complex surveys. Using the filters you can create reports you need, compare and share.


March
23
2023
Recruit is an application to manage the recruitment process of a company. If you are a company who need an application through which job seekers can apply directly on your website and you can manage those job applicants from an admin panel then this is the app you need.


March
23
2023
Appointo is an application to manage the bookings/appointments for a business. If you are a business who need an application through which customers can book appointments on your website and you can manage those appointments from an admin panel then this is the app you need.

March
23
2023
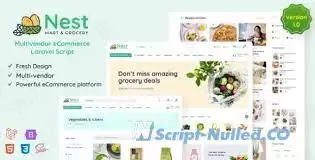
Nest is an attractive Laravel multivendor eCommerce script specially designed for the multipurpose shops like mega store, grocery store, supermarket, organic shop, and online stores selling products like beverages, vegetables, fruits, ice creams, paste, herbs, juice, meat, cold drinks, sausages, cocktails, soft drinks, cookies…

March
23
2023
Woyosis is a cloud-based platform for managing and delivering digital content. It provides your users an easy-to-use interface for creating and maintaining websites, blogs, events, jobs, appointment bookings, products and online applications, without the need for complex technical skills.


March
23
2023
ZaiwriteAI is the best AI content-writing script. Using ZaiwriteAI you can easily get more than 70+ premade templates and write content in 30+ languages. ZaiwriteAI is an advanced AI writing tool that can help you create high-quality content quickly and easily. Whether you need to write an article, a report, a blog post, or any other type of written content, ZaiwriteAI can assist you in generating unique and engaging text.


March
23
2023
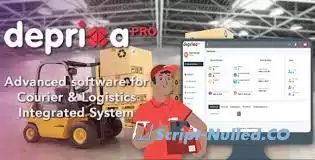
Courier DEPRIXA PRO is a software designed for companies that handle packages and purchases on the internet that require a system to monitor the logistics of storage and cargo handling to their final destination, the collection of binding modules that will create automatic billing, according to the dimensions, weight and shape of said cargo handling.

March
23
2023
DomainsKit Script is a powerful PHP-based script that consists of many great Domain & IP Tools it allows you to search domain names instantly. It has a built-in whois domain tool, domain generator tool, hostname & IP lookup tool, and domain DNS records tool. It is built with a fully responsive design based on Latest Bootstrap to ensure that your website will look flawless and beautiful on every mobile and desktop device. It also has strong cross-browser support.


March
23
2023
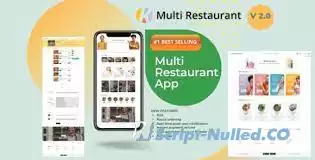
Karenderia Multiple Restaurant System is a restaurant food ordering and restaurant membership system.

March
23
2023
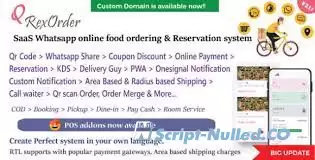
QRexOrder is a SaaS-based multi-restaurant food ordering & reservation system with payment gateways. It’s very secure, well documented, fast & user-friendly. It is mainly using to make a restaurant website and online food ordering, reservation and delivery system.

March
23
2023
Multi language options, multi currency option, 4 different payment gateways social media login & sharing, the most advanced product posting & presentation.


Site Search
Site Menu
☑ Websites Scripts
Recent comments

FiverGames Casino Platform with PGSoft Integration and Gold API
Read the documentation

Goldsvet Full Game Pack
Download, these assemblies were already here. I have added new ones to the assembly that I found

BIGGUJRAT script casino slot
You will need API, don't listen to anyone.

Gambling Platform Download 3Patti Games
Of course the code is open, what kind of stupid questions are these?

1win pro casino script Clean script from the developer with 1100 games pack
This is the original script from a former developer.
Survey on the website
Evaluate the work of the site
Tag Cloud
Popular
Statistics
- +8 Total articles 7411
- +21 Comments 5104
- +24 Users : 7483

 Spain
Spain
 Portugal
Portugal