
March
24
2023
This system helps one/multiple support agents to easily communicate with customers, keep details of all communication happening, maintain complete customer details, and many more.


March
24
2023
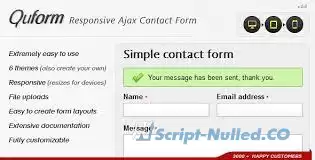
Quform is a powerful responsive ajax contact form that you can easily embed into any web page in a matter of minutes. If you need a simple contact form to put on your website Quform is sure to suit your requirements. It does everything without reloading the page which makes for a sleek user experience that is sure to make a positive impression when your visitors contact you.

March
24
2023
A cloud-based WhatsApp SAAS system where you can make a bulk campaign along with the WhatsApp bot. As this uses WhatsApp web instance so there is no hazard of banning WhatsApp.


March
24
2023
This is a module for Perfex CRM. Not a standalone script. An internal wikipedia solution to help organize and manage your knowledge resources. Intuitive, efficient, easy to use


March
24
2023
Stories is a clean and minimal Laravel blog script perfect for writers who need to create a personal blog site with simple creative features and effects to make readers feel the pleasure of reading blog posts and articles.


March
24
2023
Zaika – Ecommerce Shopping Laravel Platform PHP Scripts. it has 2 home page variant which fit anyone needs for showcase your small/medium/larage ecommerce business website. It’s highly customisable, it comes with many awesome features, like Drag & Drop Page Builder, drag & drop menu builder, drag & drop form builder, drag & drop widget builder and many more. it’s compatible with Desktop, laptop, mobile and also compatible with major browsers. it has Comes With Advance Tax/Campaign/Shpping/Coupon/Inventory module. we have added all the thing required for doing seo, seecially add og meta support for all the blog with facebook/twitter support. it support 15+ payment Gateway, Paypal, Stripe, Paytm, Flutterwave Rave, Razorpay, Mollie, Paystack, Midtrans, Mercado Pago,Cashfree, Payfast,instamojo, Bank Payment, Check Payment, Manual Payment Etc
March
24
2023
LiteHYIP, a professional HYIP Investment Solution that comes with PHP laravel. It’s developed for those people who want to start their Investment business website. There are thousands of HYIP investments scripts, many of them are not useful, some of them comes with complex user and admin interface. LiteHYIP is a simple but powerful Investment system with an easy operating system, any non-technical person now able to run their investment website.


March
24
2023
A to Z SEO Tools v2 is a Search Engine Optimization Tools. We have more than 50 SEO Tools to keep track your SEO issues and help to improve the visibility of a website in search engines. It also helps to optimize web content by analyzing content for keywords, on-site links and other SEO considerations.


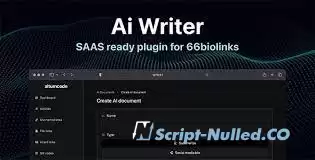
AI Writer is a plugin for 66biolinks. It is used to help people generate content with ease with the help of AI technology.

March
24
2023
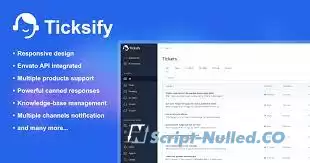
Ticksify is a simple, self-hosted and easy-to-use customer support application built with Laravel, Livewire, and Tailwind CSS. It is a fully responsive and mobile-friendly application. A perfect solution for small and medium-sized businesses to manage their customer support. It is a great alternative to other expensive customer support software like Zendesk, Freshdesk, etc.

March
24
2023
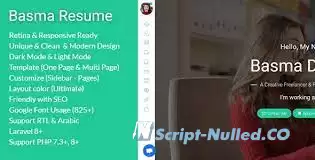
Basma Resume is a PHP system developed to build your cv or resume, It comes with clean, secured, responsive, SEO friendly & trendy look design. You can easily add your Services, Experiences, Skills, Portfolios, Blogs, Pages and More without any coding skills

March
24
2023
With our experience and state-of-the-art interface designs, we have created INFIX in School Management ERP System which is extremely reliable, intuitive, and easy to use. It can cater to all your needs of managing school, college, university and any other educational institution eliminating the tedious manual processes.

HyipPro is a automated hyip investment script for web platform. It’s a script for investment that can be used for various purposes. HyipPro comes with the features like deposits, withdraw, investment plans, bonus, referral commission, so on and so on. It is seo friendly, modern architectural and secure web application. It has very eye catchy dynamic theme for frontend, user panel and admin panel. If you are looking for hyip investment script which will gear-up your business into the next level then HyipPro will be the right choice for you. You can enjoy a lots of features along with 32 payment gateways and real-time in app notifications. We can say that this is the script which you are looking to start your hyip investment business.
Demo: https://codecanyon.net/item/hyippro-a-modern-hyip-investmet-platform/35293972
Demo: https://codecanyon.net/item/hyippro-a-modern-hyip-investmet-platform/35293972
March
24
2023
LottoLab, a laravel made Live Lottery platform that enables a great opportunity to start your own lottery website. Lotto is by far the most popular draw, in 2016, Americans spent a total of $70.15 billion on lottery tickets, according to the North American Association of State and Provincial Lotteries. we got Severals of requests to develop such items and we collect idea’s from some popular platforms and clients. No need to pay thousands of dollars to hire developers to build your Lottery Website. LottoLab may assist you to handle unlimited Tickets, Lotteries, draws, Winners, able to accept payment via cards, cryptos, and mobile money. the ready-to-go solution, it takes only a few minutes to set up your website with our system.
March
24
2023
eCart is a frontend web version of the most popular ecart Android solution available on codecanyon.


Site Search
Site Menu
☑ Websites Scripts
Recent comments

FiverGames Casino Platform with PGSoft Integration and Gold API
Read the documentation

Goldsvet Full Game Pack
Download, these assemblies were already here. I have added new ones to the assembly that I found

BIGGUJRAT script casino slot
You will need API, don't listen to anyone.

Gambling Platform Download 3Patti Games
Of course the code is open, what kind of stupid questions are these?

1win pro casino script Clean script from the developer with 1100 games pack
This is the original script from a former developer.
Survey on the website
Evaluate the work of the site
Tag Cloud
Popular
Statistics
- +6 Total articles 7411
- +23 Comments 5104
- +26 Users : 7483

 Spain
Spain
 Portugal
Portugal


