March
25
2023
SaaS Theme is the perfect theme for Premium URL Shortener SaaS version. It comes with many unique features including a dedicated control panel in the admin panel where you can change the skin, control testimonials and your corporate address.


March
25
2023
66biolinks (former phpBiolinks) is the only social bio link platform you’ll ever need, including a fully-featured URL Shortener & a QR Codes system.

March
25
2023
“Businesso” is a Business / Ecommerce Website Builder SAAS (Multitenancy). You can use Businesso to build business / ecommerce website builder within minutes. The business website frontend is Multi-lingual & also RTL supported You can create unlimited monthly / yearly / lifetime packages, control features for that packages. You can make a package Free, Trial, Premium or only free or only trial or only premium. You can set trial days for trial packages.

March
25
2023
GeniusWallet is the Advanced Professional Wallet CMS that has all the necessary features to start a Wallet with Payment Gateway API based on Laravel. Mainly its developed for those people who want to start their Business in Professional Wallet System. You will get an API System, and you can easily connect your wallet with other websites in a short time. If you are looking for Complete Professional Digital Wallet Business then it’s a great choice for you. Your Genius Wallet can easily handle Unlimited Users, Transactions, Deposits, Withdraw, Merchant, and many more required Features for a Great Wallet System. Its Supports Multiple Payment Gateway, Multiple Languages, Multiple Currency, Multiple Staff, and Lots of Advanced System Like Secret login, KYC Consent, Module Management and many more.
March
25
2023
Ultimate SMS is a powerful, flexible, and User-friendly Bulk SMS Marketing Application. It’s also an all-in-one solution for your SMS marketing. It’s easy to use & install.


March
25
2023
SMM Matrix is a social media marketing tool. This software includes almost everything for you need to do a social media marketing business. It has services lined up for every social media platform and hence is a very versatile platform. Be it likes, followers, views, or even general engagement or website traffic, SMM Matrix can get it all, and that too at a price that does not burn a hole in your pocket.

March
25
2023
Writerifly – The ultimate content generation tool that can help you produce high-quality, engaging content quickly and efficiently. Our script use OpenAI to generate hight quality content.

March
25
2023
AiWriter is an AI-powered content writing tool for the Laravel framework. It uses advanced machine learning algorithms to analyze and understand text, allowing it to generate high-quality, unique content for your website or application. With AiWriter, you can easily create engaging, SEO-friendly content for blog posts, articles, and more, saving you time and effort while improving your online presence. Whether you’re a blogger, a marketer, or a developer, AiWriter is the perfect solution for all your content creation needs.

March
24
2023
AiWriter is an AI-powered content writing tool for the Laravel framework. It uses advanced machine learning algorithms to analyze and understand text, allowing it to generate high-quality, unique content for your website or application. With AiWriter, you can easily create engaging, SEO-friendly content for blog posts, articles, and more, saving you time and effort while improving your online presence. Whether you’re a blogger, a marketer, or a developer, AiWriter is the perfect solution for all your content creation needs.

March
24
2023
ChatPion mainly is a visual drag and drop Flow Builder based chatbot for Facebook Messenger and Instagram DM. It also comprises a feature for auto comment, auto-reply to comment, and private reply for Facebook and Instagram. Besides, It has a feature for posting on Facebook, Instagram, and others. True, it has an SMS and Email marketing service. On the other hand, it has a full-featured Ecommerce that can live inside Facebook Messenger, Instagram DM, and on web browsers. And ChatPion is a self-hosted white label multi-user SaaS application. In one word, it is an all-in-one marketing solution for your business.
March
24
2023
Pixer – React Laravel Multivendor is a digital eCommerce Marketplace script implemented based on Laravel, React, Next JS, and Tailwind CSS. It is one of the fastest and most secure digital assets selling E-commerce app. It’s very easy to use, we have used axios and react-query for data fetching. You can set up your API endpoints very easily and your frontend team will love using it. It has REST API support.


March
24
2023
Malware Scanner will help you to scan your website with one simple click. It can find both known and unknown viruses, shells, malware, malicious code infections and other website threats.

March
24
2023
WhatsIPs is an IP address Lookup PHP Laravel Script and IP address based geolocation finding system. Free 50,000 query per month. It’s works for both IPV4 and IPV6. The system also shows the location on google map, ISP name, Hostname, Proxy Information, Continent, Country & Region Information, latitude & longitude, and more. It’s a Furnish, Ready to Use, SEO ready, Google Adsense and Custom Ads ready and referral/affiliate links ready Script or tools for earning money. You can easily build a website or online tools like whatismyip just install this script in your server and start earning with it by showing Google or Custom Ads and referral/affiliate links. It has a powerful admin panel to control the tools. Anyone can easily update/edit this system by following our Well Sorted Documentation.
March
24
2023
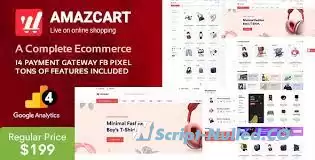
AmazCart is a complete E-Commerce system to easily start your online E-Commerce business. This Software has been developed for people who want to create an online store that can sell everything! Single eCommerce store. AmazCart’s online store will make you successful in the eCommerce industry as well as will save thousands of marketing costs even don’t need any coding skills. (Multi-vendor – sold separately)

March
24
2023
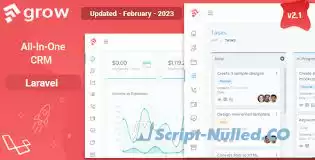
Grow is a client relationship management application, with full project management features. Grow combines many of the various tools that you require, in one easy to use application. These include task, invoices, leads, estimates and much more.

Site Search
Site Menu
☑ Websites Scripts
Recent comments

FiverGames Casino Platform with PGSoft Integration and Gold API
Read the documentation

Goldsvet Full Game Pack
Download, these assemblies were already here. I have added new ones to the assembly that I found

BIGGUJRAT script casino slot
You will need API, don't listen to anyone.

Gambling Platform Download 3Patti Games
Of course the code is open, what kind of stupid questions are these?

1win pro casino script Clean script from the developer with 1100 games pack
This is the original script from a former developer.
Survey on the website
Evaluate the work of the site
Tag Cloud
Popular
Statistics
- +5 Total articles 7411
- +22 Comments 5104
- +26 Users : 7483

 Spain
Spain
 Portugal
Portugal


