Jork is a modern design created for creative agencies. With this template you can make all kinds of mixes as your imagination takes you.
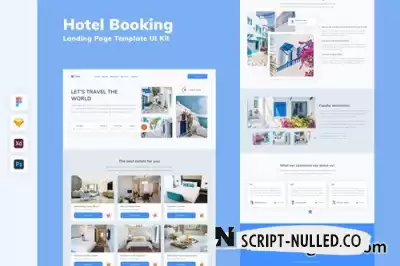
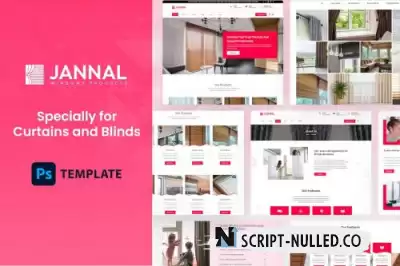 Jannal is a charismatic and mesmerizing PSD designed for blinds, curtains and furniture store websites. This template will surely give a glow to your potential client’s eyes with its polished, fresh and unique design! With colorful and field focused layouts like service, price, shop, and team you can easily draw the visitor’s attention and keep them always on your webpage.
Jannal is a charismatic and mesmerizing PSD designed for blinds, curtains and furniture store websites. This template will surely give a glow to your potential client’s eyes with its polished, fresh and unique design! With colorful and field focused layouts like service, price, shop, and team you can easily draw the visitor’s attention and keep them always on your webpage.
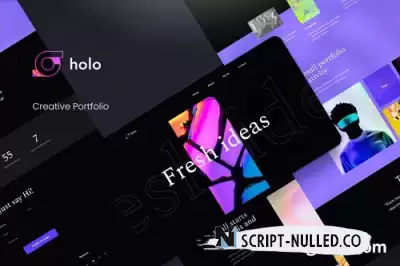
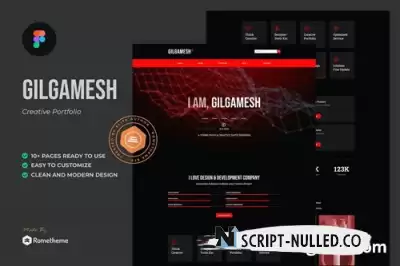
Meet, Gilgamesh is specially designed for Personal & Creative Agency websites! The template kit comes with an ideal selection of templates for any business related to Personal & Creative Agency Services services. This Figma template has a modern and unique design layout and is sure very easy to customize.
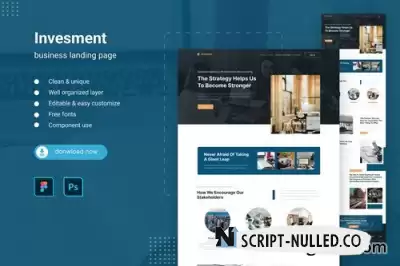
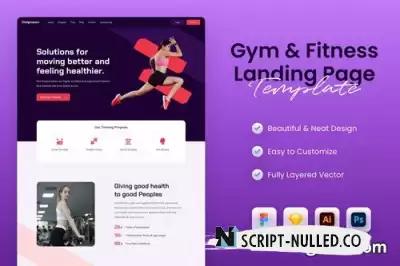
 It is a landing page design template for some niche marketing campaigns. This template was created based on the requirements of the industry.
It is a landing page design template for some niche marketing campaigns. This template was created based on the requirements of the industry.
100% Vector and editable
Compatible with Sketch, Figma, Adobe Photoshop, Adobe Illustrator
Free Fonts Used (See PDF)
Thanks for downloading our product!
Notes Images are just for preview purposes only; they are not included in the download files.
18 awesome quality Fashion Sale Web Banner template PSD files, including Facebook & Instagram ad sizes, ready for your Services, products, campaigns. Each PSD file is layered and fully organized. You can use these banners for Google AdWords & social media too. ( Facebook & Instagram ad sizes included )
Site Search
Site Menu
☑ Websites Scripts
Recent comments


Survey on the website
Evaluate the work of the site
Tag Cloud
Popular
Statistics
- +20 Total articles 7411
- +70 Comments 5165
- +21 Users : 7488

 Spain
Spain
 Portugal
Portugal