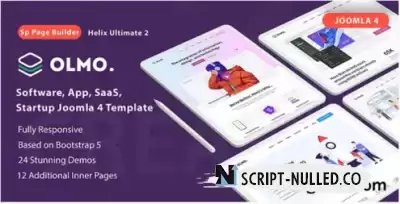
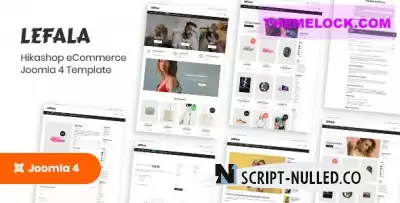
Make your fashion statement with Lefala, a template we designed for every modern fashion clothing and luxury brand. The template comes packed with an astounding selection of ecommerce, jewelry, streetwear, glasses store, fragrance and perfume store templates, which makes it an ideal choice for every fashion store website out there.
Golden hearts is a creative and inherently flexible theme designed to make a solid and respectable online platform for a variety of projects relating to NGOs, charity events, campaigns. Spread the awareness for a cause in a professional way with this template and popularize your organizations today.
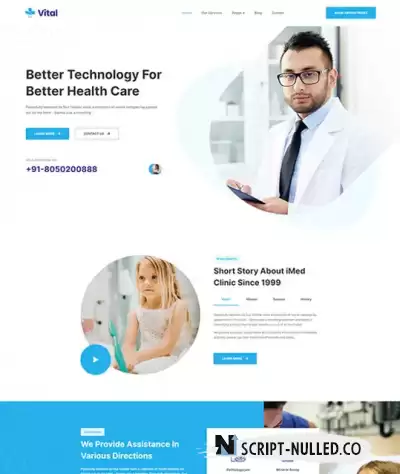
JA Vital is a professional Joomla template for Hospitals, and Health Care centers, featuring cosmetic clinics. Its oriented & creative design, many beautiful content blocks to represent your website content in smart layouts. The medical Joomla template provides specifically designed sections and pages for Healthcare website: Department directory, Services, Doctors, and beautiful bonus pages: Blog, Contact, and all Joomla default pages with customized style to fit the template design. The Joomla medical template is built with the robust T4 Joomla Template Framework, fully responsive at core, optimized for SEO and performance. It supports Acymailing for newsletter signup and marketing plans.
Uber is the perfect All in one Joomla template to help everyone build their business site. This special Joomla template is a feature project for Joomla 3 & Joomla 2.5. It is a built with T3 Framework template with Bootstrap 3, and the Advanced Custom Module. Uber is the first JoomlArt template to sport on the brand new Joomla extension JA Advanced Custom Module (JA ACM). With JA ACM, one can build a whole website from the scratch with multiple content blocks for Testimonials, CTA, Gallery, Slideshow, Pricing Table, Features Intro, etc. Just choose the blocks you desire and start to connect them. Uber is now one of the most powerful responsive Joomla template, a Swiss knife for Joomla sites building with 18+ content blocks, 80+ variations, 17+ sample sites, and thousands of possibilities.
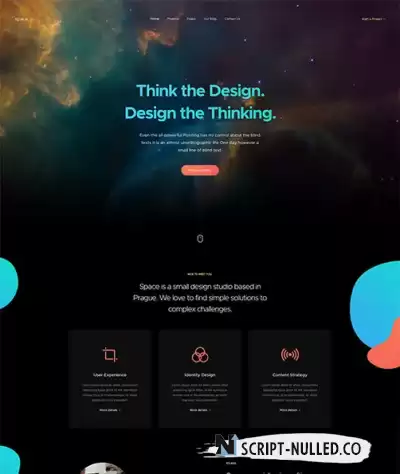
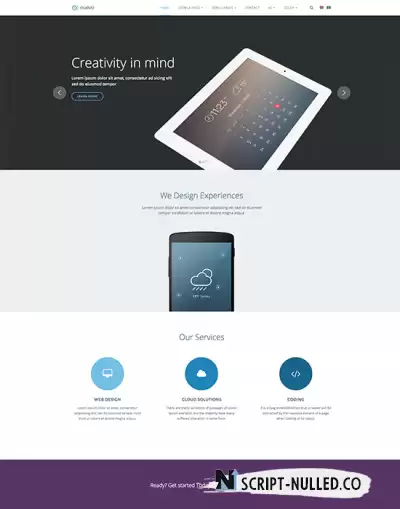
JA Space is creative and modern Joomla template for portfolio, agencies, corporate and business website with clean, elegant design and amazing effect. The portfolio template supports dark theme and light theme, Joomla custom fields and beautiful additional pages. You can impressively showcase all your projects, portfolio in the elegant projects page with grid layout, image gallery, Joomla custom fields. The portfolio Joomla template is responsive for the full experience on any device or screen-size, supports all default Joomla pages and more.
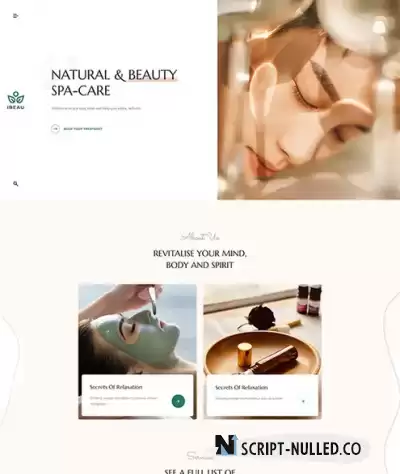
Looking to open a beauty business? We’ve got you covered! Welcome to our JA Spa - a creative and fancy beauty Joomla template, designed for beauty parlor, hair salon, nail salon owners. It offers multiple ready-to-use pages: Homepage, service list, service details, blog with details and a special full-screen menu. The beauty Joomla template is developed on JoomlArt's T4 Framework that utilizes the latest Bootstrap 4 library, fully-responsive and advanced template dashboard with amazing features: layout builder, mega menu builder, theme custom tool and many more.
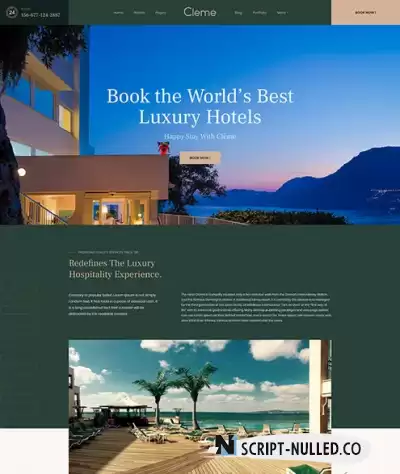
JA Resort is an incredibly beautiful, modern, and creative Joomla template designed for hotels, guest houses, motels, service apartments, and any other kind of accommodation website which requires a booking system. It fully supports the most popular and advanced hotel booking extension: Solidres. JA Resort is built with the all-new T4 Framework, supports many beautiful website content elements to show content in beautiful layouts. It supports multiple addition pages: About us, Blog, and all default Joomla pages. The Resort and hotel booking Joomla template provides native RTL (Right-to-Left) language support for special languages: Arabic, Persian, and others.
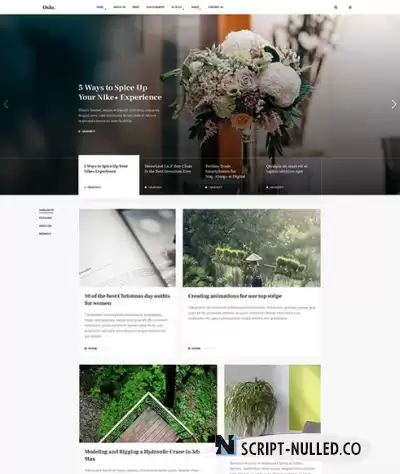
JA Oslo is a dedicated News and Magazine Joomla template with creative design and ultimate core features, it includes all required pages for a News and Magazine website, multiple them colors and supports flexible menu system with Megamenu, Mobile dropdown menu and Off-canvas. The template is fully responsive based on Bootstrap 3 responsive grid system. JA Oslo has 2 color themes: Dark and Light to give you more choices for your website. The Joomla template is built with robust T3 framework. It has intuitive admin panel with built-in functionalities and tools: visual layout configuration, theme setting, megamenu builder, compression, etc.
The App page responsive Joomla template for Joomla 3 & Joomla 2.5 - JA Nuevo is dedicated for apps startup or services page. It's a T3 Framework template with Bootstrap 3, RTL Language Layout, K2 Component, and responsive. JA Nuevo is modern design template with lot of whitespace and simplicity. It helps enhance the performance of a landing page, improve readability and make a bold first impression. JA Nuevo is flexible with robust tools, you don't have to be CSS ninja, or PHP geek to do the customization. JA Nuevo is a must have Joomla template for app page, business, services, or landing pages. This template supports RTL language layouts.
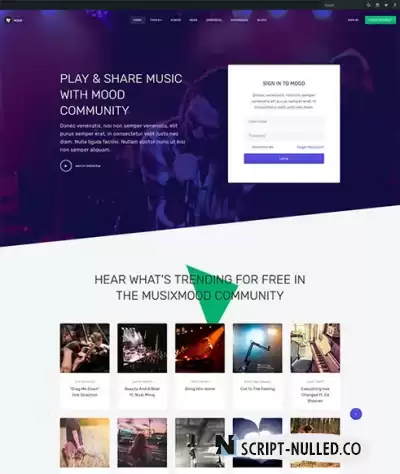
Music, community, social network Joomla template - JA Mood fully supports JomSocial and EasySocial component. JA Mood comes with creative design, integrates JA Joomla page builder to create landing pages, outstanding pre-made additional pages: Videos, News, Blog and support all Joomla default pages with customized styles. JA Mood is based on powerful T3 Framework, it is fully responsive, ease of customization and intuitive admin panel with powerful built-in functionalities: Megamenu builder, Visual layout configuration, theme settings, etc.
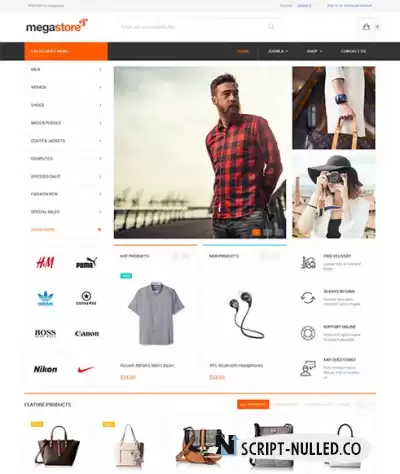
JA Megastore is an advanced eCommerce responsive Joomla template based on Free Joomla eCommerce component - Virtuemart. The template supports all shop pages with clean and creative design to show off products in smartest ways. The Virtical Megamenu is a great additional feature to organize products in your site better. The Virtuemart template is built with robust T3 Framework and new web technologies, it is fully responsive based on powerful Bootstrap 3 responsive grid system. JA Megastore is SEO friendly and optimized codebase to make it perform better. The intuitive theme control panel with core features built-in will help you manage the site with ease.
JA Mason is a creative Joomla template for company and business websites, supports light and dark theme color, vertical and horizontal menu style, flexible layout system, and a number of beautiful pre-made pages: Projects, Blog, Contact. The business template also supports all Joomla default pages. The Mason Joomla template is fully responsive, built with robust T3 Framework, integrates Bootstrap 3.
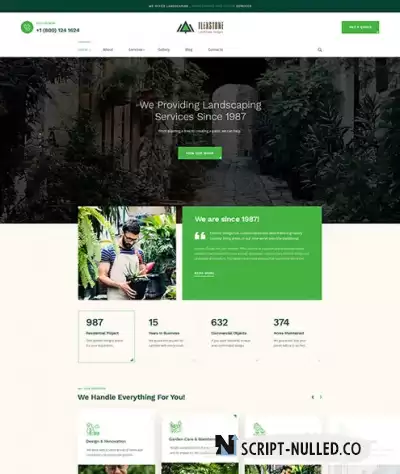
JA Landscape is a premium Joomla Template dedicated designed for gardening business, landscaping company, gardeners, exterior designer, lawn service website with modern design, impressive page elements including slideshow, features intro, services, testimonial, clients and more built with JA ACM module for ease of configuration. It also comes with a beautiful ready-to-use portfolio (projects) and services page.
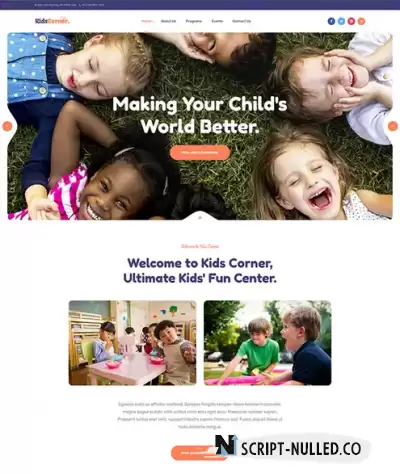
JA Kids Corner is a complete solution for Children's play center, kids education, kindergarten websites with creative and colorful design style. JA Kids Corner template fully supports DT Register - an advanced Joomla events booking extension to build Events and Programs booking system with 40 popular payment gateways support and onepage checkout. The kids center Joomla template is based on T3 Framework, fully responsive, supports megamenu, flexible layout system, visual layout configuration and more.
Site Search
Site Menu
☑ Websites Scripts
Recent comments


Survey on the website
Evaluate the work of the site
Tag Cloud
Popular
Statistics
- +22 Total articles 7411
- +72 Comments 5165
- +22 Users : 7488

 Spain
Spain
 Portugal
Portugal