Osintgram is a OSINT tool on Instagram. It offers an interactive shell to perform analysis on Instagram account of any users by its nickname

Osintgram is a OSINT tool on Instagram. It offers an interactive shell to perform analysis on Instagram account of any users by its nickname

An ongoing collection of awesome tools and frameworks, best security software practices, libraries, learning tutorials, frameworks, academic and practical resources about Open-source intelligence (OSINT) in cybersecurity.

Information security (IS) is one of the most in-demand areas of IT. In this article, you will learn about the professions of IB and how to switch to IB with any background.

Open Source Intelligence (OSINT) Analyst adalah seseorang yang memiliki kemampuan, keterampilan, serta daya analisis yang terstruktur dan tepat dalam mendapatkan. mengumpulkan, dan membuat laporan tentang informasi yang terpublikasi di internet untuk keperluan perusahaan, lembaga, keamanan, dan pertahanan.

What is social engineering and how did it come about?
Social engineering or "attack on a person" is a set of psychological and sociological techniques, methods and technologies that allow you to obtain confidential information.

A denial of service (DoS) attack is an attempt to cause harm by making a target system, such as a website or application, inaccessible to ordinary end users. Attackers usually generate a large number of packets or requests, which ultimately overload the target system. To carry out a distributed denial of service (DDoS) attack, an attacker uses a variety of hacked or controlled sources.

Any website is vulnerable to intruders and is not immune from hacking. It is not necessary that the purpose of virtual criminals is to steal data or access user accounts. The site can be used as a repository of their information, usually illegal. With the help of a stolen resource, they can spread spam, engage in mining, and extortion.

Anonymity on the Web is a burning topic for discussion. We use many services every day that track our IP address. In fact, this is our real physical address, which is easy to establish. Imagine that you are walking down the street with your home address printed on your shirt. The same thing happens when you browse the internet without masking your location. Not everyone likes it. Read the best article on how to stay anonymous online

My cryptocurrency was stolen. What to do?

Content
Levels of anonymity
Rules of online behavior
Methods of obtaining information about you and how to resist them
In conclusion
Anonymity is important for all Internet users. Neglect can lead to personal data and photos falling into the hands of intruders, to the loss of money from electronic wallets and bank cards. Therefore, everyone should know the basic rules of anonymity.

To ensure the confidentiality of personal data and weaken control over your personal life on the Internet (social networks, chat rooms), you need to think about countering the identification of your computer on the network.

The better the site, the more attacks there are on it. Unfortunately, this is the harsh reality of the Internet.
We don't want to brag, this dependence is reflected in our products: customers often complain about attacks; but we prevent them in time by building protection against hacking at the stage of its development.

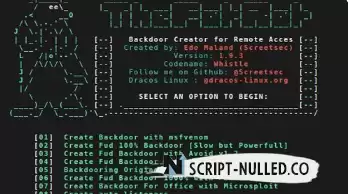
Thefatrat is a massive tool that allows you to bypass most antivirus programs.
A simple tool to create a backdoor to bypass AV and a lightweight tool for a post-exploitation attack such as a browser attack, DLL.
This tool compiles malware with a popular payload, and then the compiled malware can be run on Windows, Android, Mac.
Mobile operators receive a lot of data and metadata, which can be used to learn a lot about the life of an individual subscriber. And by understanding how this data is processed and stored, you will be able to track the entire chain of information passing from the call to debiting money. If we talk about the internal intruder model, then the possibilities are even more enormous, because data protection is not at all part of the tasks of the mobile operator's pre-billing systems.
Definition of hacking
Hacking is a set of actions to identify and then exploit vulnerabilities in a computer system or network, usually in order to gain unauthorized access to user or company data. Hacking is not always the result of malicious actions, but the term itself has acquired a negative connotation due to its frequent use in the context of cybercrime.


