
Game Modes: Dice Mines Bubbles Wheel Slots The script is fully working, ready for opening. It was pumped out from the Stimul server itself, there are no bugs and holes. Instructions are in the archive.

Game Modes: Dice Mines Bubbles Wheel Slots The script is fully working, ready for opening. It was pumped out from the Stimul server itself, there are no bugs and holes. Instructions are in the archive.
Concept behind Seeker is simple, just like we host phishing pages to get credentials why not host a fake page that requests your location like many popular location based websites.
Social engineering tool [Access Webcam & Microphone & Location Finder] With {Py,JS,PHP}

I want to share what I know about DDoS — what kind of attacks they are, what they are, how to prevent them and minimize the impact of such attacks on your service.

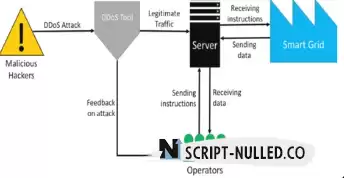
DDoS Amplification Tool
When the Internet appeared, there were no questions about anonymity. Then everyone who was online turned into a virtual character, who had almost nothing to do with the real person sitting at the computer. To ensure complete anonymity on the web, it was enough just to use aliases instead of real data. That's what everyone did.

Incredibly fast crawler designed for OSINT.

OSINT (Open Source Intelligence) – collection and analysis of information from publicly available sources. In the current reality, we are talking mainly about Internet sources. From Russian-speaking experts, you can hear the term "Internet intelligence", which is equivalent to OSINT in meaning.

Witchcraft Online is a social engineering tool with sub-functions that aim to meet people's social needs, such as social media services and short message services.
Launched attacks are always associated with spam (resending messages), spoofing and brute force engineering, since dos or denial of service subfunctions are nothing more than just attracting interested users.

Currently, software protection methods based on the use of cryptographic algorithms are widely used. Regarding the effectiveness of protection of this class, I would like to cite the opinion of Chris Kaspersky, author of the book "The Technique and philosophy of hacker attacks": "These defenses look unbreakable. They "look" because developers do not take into account the difference between theoretical models and practical implementation... a lot of the cryptosystems used are unreliable, and almost all are vulnerable to one degree or another"[20, p. 30].

TOR Bot Dark Web OSINT Tool
A distributed DDoS attack is carried out simultaneously from a large number of devices - attackers gain control over them and generate streams of garbage requests on command. Such an attack can cause a denial of service to the systems of a large company or network.

Tool Information Gathering & social engineering Write By [Python,JS,PHP] DarkSide



